How Can You Defend Against a Threat That is 64 Times Worse Than Ransomware?

This Threat is Knocking on Your Door – Can You Stop It?
Cybersecurity makes headline news these days. Major cyberattacks are certain to be prominently featured by news organizations, and media outlets love to serve up all of the dirty details of a splashy ransomware incident or a shadowy nation-state cybercrime action. But those headlines aren’t trumpeting the damage of a potentially ruinous threat that is 64 times worse than ransomware yet often flies under the radar: Business Email Compromise (BEC).
See how to avoid cybercriminal sharks in Phishing 101. DOWNLOAD IT>>
BEC is 64 Times Worse Than Ransomware
That number isn’t based on speculation. It’s a conclusion supported by the facts laid out by this year’s internet crime report from the FBI’s Internet Crime Complaint Center (IC3). FBI cybercrime analysts determined that business email compromise (BEC) schemes were the costliest cybercrime reported to IC3 in 2020, clocking in at 19,369 complaints with an adjusted loss of approximately $1.8 billion. The rest of the list features larger numbers of reports but nowhere near the same financial damage. Phishing slotted in at number two for adjusted loss with 241,342 complaints that added up to over $54 million. The number of ransomware incidents reported to the FBI also continues to climb, with 2,474 incidents reported in 2020. IC3 was careful to note that it doesn’t receive reports of all scams in a given year.
Cybercrime Reported to FBI IC3 Sorted by Victim Loss
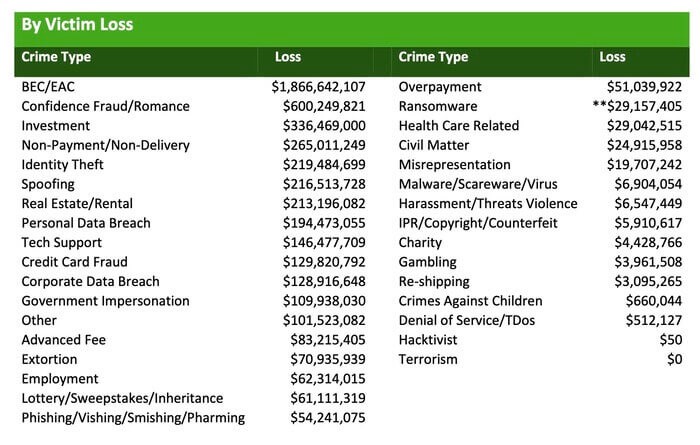
All told, BEC was responsible for 37% of all cybercrime losses last year, pulling down an estimated unadjusted total of $2.1 billion. Yet ransomware is typically portrayed as the star of the show. It only accounted for 1% of cybercrime loss, making BEC 64 times worse than ransomware for a company’s bottom line.
We’ll show you how to spot security risks fast with employee profiling! SEE THE DEMO>>
Spoofing: BEC’s Best Friend
That total figure includes spoofing as well, which IC3 scores separately. Many BEC attacks also include spoofing, a technique that ballooned by more than 220% in 2020. Spoofed email accounts or websites were the most commonly seen assets used in BEC attacks against businesses in 2020, with 71% of organizations admitting they had seen one over the past year. Some of the biggest brands that employees encounter in their daily lives are common victims of email spoofing. It doesn’t take much effort for a cybercriminal to use a cloned email from a legitimate sender and alter the details enough to garner an unsuspecting click as part of a lucrative BEC campaign. Altogether, nearly $217 million in business cybercrime losses were the result of email spoofing.
In just the last few years, major campaigns have included:
- PayPal phishing
- Amazon phishing
- FedEx phishing
- Lastpass phishing
- Walmart phishing
- Walgreens Phishing
- USAA phishing
BEC and Brand Impersonation Go Hand in Hand
Brand impersonation, a subset of spoofing is also rampant as a BEC support player. A specialized form of spoofing, brand impersonation Some of the biggest brands that employees encounter in their daily lives are common victims of email spoofing and brand impersonation. It doesn’t take much effort for a cybercriminal to clone an email from a legitimate sender and alter the details enough to garner an unsuspecting click.
Bad actors are savvy when choosing their spoofing fodder. They typically turn to brands that businesses trust and brands that employees interact with regularly.
The list of the most imitated brands of 2020 includes:
- Microsoft (45 percent)
- DHL (18 percent)
- LinkedIn (6 percent)
- Amazon (5 percent)
- Rakuten (4 percent)
- Ikea (3 percent)
- Google (2 percent)
- PayPal (2 percent)
- Chase (2 percent)
- Yahoo (1 percent)
What’s next in phishing? Find out in the 2021 State of Email Security Report! GET IT NOW>>
BEC Scams Are Chameleons
Another major problem that IT professionals face when confronting the threat of BEC is the variety and complexity of the attacks. This is not a simple, easy-to-spot scam. In just the last few months, a panoply of BEC scams directed at a wide range of targets have demonstrated exactly why BEC is such a slippery foe. Unfortunately, these sophisticated fraud attempts have a high rate of success because of the careful social engineering that goes into them. 2020’s bumper crop of BEC scams was also greatly assisted by the high email volumes and uncertainty experienced by a flood of email-dependent remote workers. These injurious BEC attacks are a great example of the wide variety of schemes that cybercriminals are cooking up:
- An average employee at an Iowa company received emails in May 2019 that appeared to be from their contact at a legitimate Texas company that the Iowa firm did business with regularly. In these falsified messages, the Texas company billed the Iowa company for a legitimate outstanding invoice that was due for payment. But the message also told the Iowa company that the Texas company’s banking information had changed, and payment needed to be sent to a new account. The Iowa company ultimately made two wire transfers totaling more than $265,000 before anyone at either company discovered that they’d been victimized in a BEC scam.
- The Town of Peterborough, New Hampshire, lost $2.3 million after scammers tricked town employees into sending large payments to the wrong accounts. After the local school system complained that it had not received the funds that had been earmarked for it, investigators discovered that scammers had used spoofed email accounts and forged documents to redirect the town’s payment to accounts under their control. Several other payments to municipal departments and contractors had also been snatched by the same cybercriminals. The total loss to the town was $2.3 million almost 15% of its yearly budget.
- Wall Street investors haven’t escaped the sight of BEC practitioners. In one sophisticated scam, BEC actors masquerade as investment firms to contact send fake capital call notices marks that typically engage in stock trading. They then demand that those marks must immediately transfer funds to fulfill the obligations of their investment commitment, typically via wire transfer. These big game BEC scams employ social engineering just like a run-of-the-mill BEC operation, using dense legal language to enforce the payment demand – except fake capital call scams have an average targeted payout of a whopping $809,000, seven times the payday of a typical BEC scam.
Still relying on an old-fashioned SEG? See why Graphus is better! SEE THE COMPARISON>>
How to Protect Businesses from BEC Scams
Guarding against BEC scams has to be a top priority for every organization. But it doesn’t have to be something that requires a great deal of time and effort from employees, especially chronically overworked IT teams. By choosing automated, AI-powered email security using Graphus, businesses gain strong protection from phishing-based threats like BEC that doesn’t need help from humans or damage the bottom line.
Sophisticated socially engineered BEC threats don’t stand a chance against smart the triple-layered protection that is provided by Graphus. A powerful defense against phishing starts with TrustGraph, our patented AI-powered automated guardian that spots and stops dangerous messages before they ever reach an employee inbox.
How does Trustgraph get the job done? The secret to its success is that it doesn’t just compare incoming messages against a safe sender or subject list like many conventional email security solutions. Instead, TrustGraph relies on a smart AI that independently adjudicates everything about each unique incoming message, including content and attachments, using more than 50 points of comparison to sniff out fakes.
TrustGraph also doesn’t rely on humans to constantly apply patches or feed it threat reports to find and stop new threats, even zero-day threats. The AI never stops learning, collecting its own intelligence and making automated protection with Graphus more effective than conventional email security or a SEG. Email security using an automated solution like Graphus prevents 40% more phishing messages from reaching employees than any other type.
Don’t spend valuable time and energy on keeping up with the latest intelligence about BEC scams in order to remain vigilant. Stop phishing immediately with Graphus – the most simple, automated and affordable phishing defense available today to keep BEC scams away from every business.






