Sophisticated Voicemail Phishing Attack Detected by Graphus
Recently we detected a voicemail phishing attack where the hacker made adjustments to their attack methods to try slip by detection technologies. These adjustments were smart enough to get past existing security tools such as Microsoft’s ATP, but not Graphus®!
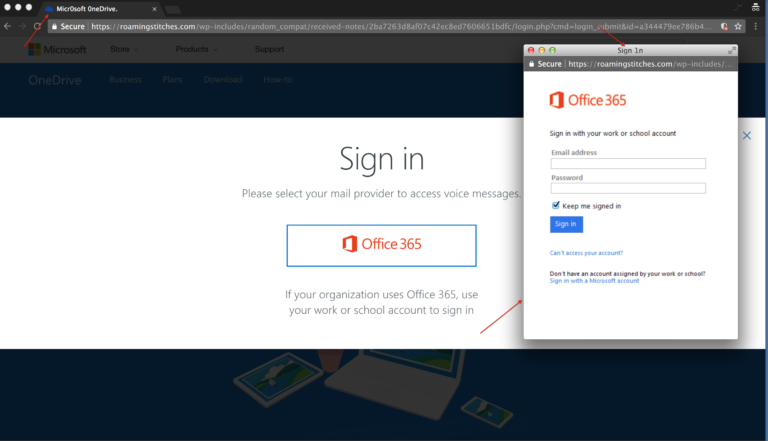
The recipients received an email saying they had a voicemail and to login to their account to listen to the message. Below is the phishing site recipients were taken too. At first glance it looks like your typical Office 365 login screen but let’s break this down a bit further.
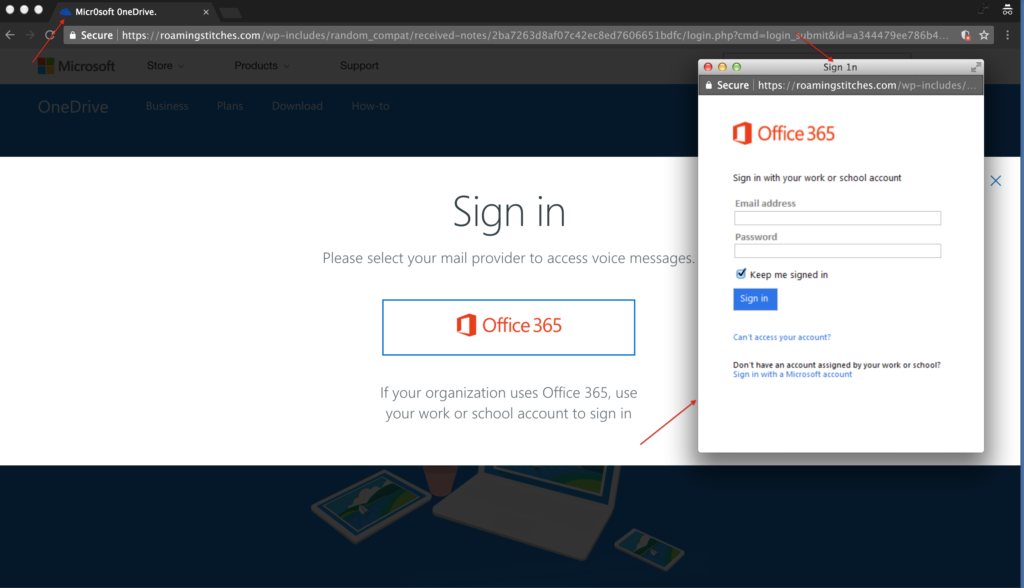
First, they hid the login screen. The recipient had to click on the Office 365 button which displays a pop-up login screen. This is the first attempt to get past existing security tools because if the button was replaced with the form asking for credentials, it would have been easier for other technologies to detected this attack – but these attackers aren’t in the business of making things easy to detect.
Second, the popup screen is not a regular HTML page but an image to avoid any text parsing software. Why is this so important? Because most detection methodologies use text based machine learning. These detection methodologies would be able to parse an HTML page, extract text, and apply the machine learning to detect that this is a suspicious or malicious site. But these methods do not work for images, and the attackers know this.
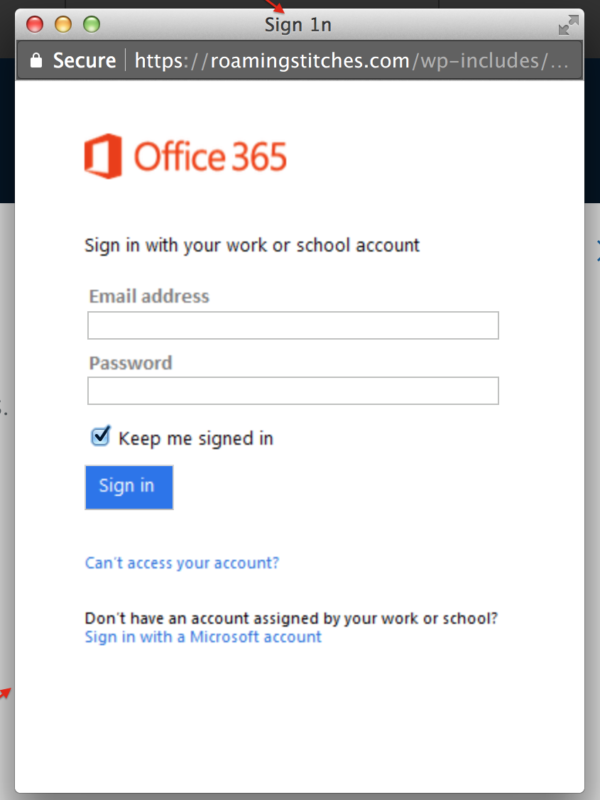
Next, they misspelled “Sign In” to read “Sign 1n” to again fool text parsers.
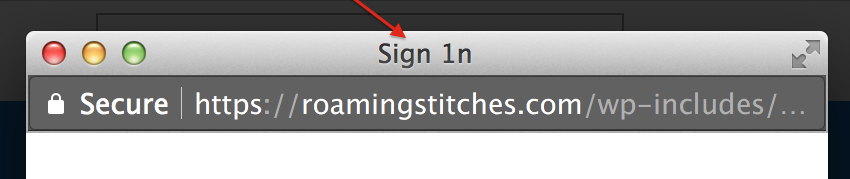
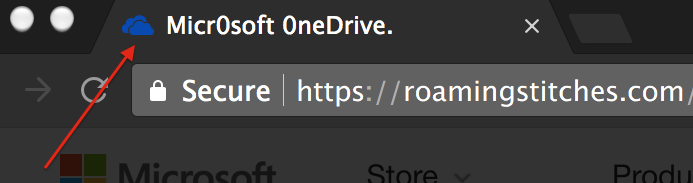
Lastly, they misspelled Microsoft OneDrive. They used zeros instead of “O’s”. This was to also fool text parsers. These deliberate spelling mistakes would throw off the text based machine learning software and easily go undetected.
Attackers are constantly looking for ways to (1) make sure their message reaches your employees and (2) make sure the messages are as legitimate looking as possible to get them to respond or provide credentials. Relying on outdated detection methodologies such as text parsing, sender reputation, threat intelligence, DMARC, and other mechanisms makes your organization extremely vulnerable to sophisticated attacks. Come out of the stone age and get protected today with Graphus®!






