Watch Out for Brand Impersonation Phishing Attacks

Holidays are the perfect opportunity to destress. We all plan to spend quality time with our loved ones, check off some of our vacation goals and prepare for the coming year’s hustle. But, somewhere in the shadowy alleys of the dark web, cybercriminals are making their holiday plans too, and those include launching sophisticated phishing attacks that can spoil your holiday season. Brand impersonation phishing or spoofing is one of the most devious ways that cybercriminals use for their phishing escapades, and they’re especially prevalent this time of year. Businesses must take proactive action now to approach this problem and quickly bolster their security to avoid dire consequences.

Get the guide that helps you detect & defeat dangerous BEC attacks to keep your company out of trouble! DOWNLOAD IT>>
What is a brand impersonation attack?
Brand impersonation attacks are a type of phishing attack in which bad actors pose as a trusted company or a brand to trick victims into giving the scammers money or disclosing personal or otherwise sensitive information. Attackers often use domain and email spoofing to lure an unsuspecting target into believing that the email comes from a trusted source. According to a report, 25% of all branded emails companies receive are spoofed or brand impersonation attempts. Also, due to the significant online presence of organizations across industries, cybercriminals are launching sophisticated brand impersonation attacks in various sectors.
Brand Impersonation Attacks Across Industries in 2022
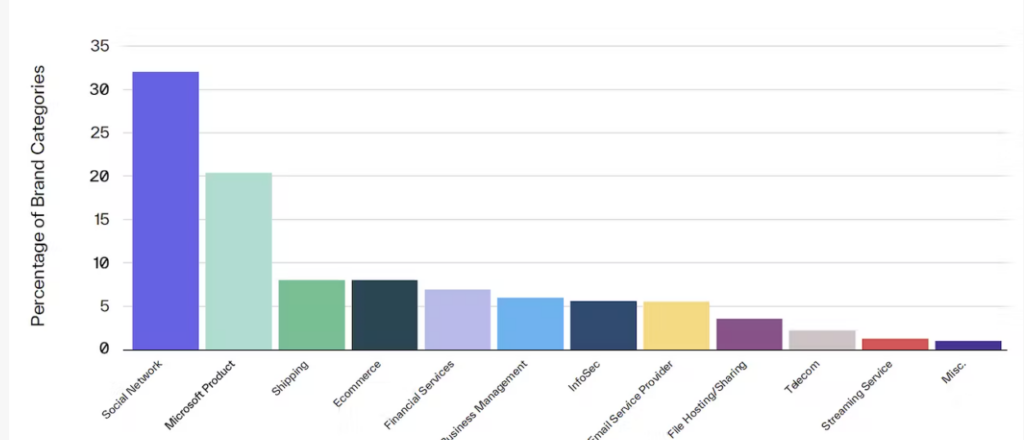
Source: H2 2022 Email Threat Report

Is your email security solution really getting the job done? This checklist helps you find out! GET CHECKLIST>>
Why is this a problem for businesses?
Let’s face it: everyone does a little holiday shopping on their work devices. With the growing number of online platforms and apps that people visit for shopping, travel and communication throughout the holiday season, cybercriminals have gained the opportunity to drive brand impersonation attacks to menacing levels. Additionally, people receive a flood of branded email messages during the holiday season, when they tend to be distracted, making them more likely to make a mistake handling email. One misclick is enough to open the door to many email-borne cyberattacks like ransomware or other malware. Plus, credential compromise risk rises, especially if people reuse passwords that aren’t protected.
Unfortunately, cybercriminals know all of this, and they’ve already started their campaigns in advance of Black Friday. They’re gearing up for a busy season of spoofing using sophisticated email templates that resemble emails from top brands that can easily convince victims to give up their credentials. In fact, IBM’s Threat Intelligence Report states that Microsoft, Apple and Google were the top three brands, criminals attempted to impersonate. They used these mega brands repeatedly in phishing kits to capitalize on their popularity and the trust many consumers place in them.
Top 11 Most Spoofed Brands
- Microsoft
- Apple
- BMO Harris Bank (BMO)
- Chase
- Amazon
- Dropbox
- DHL
- CNN
- Hotmail
Source: IBM

See the state of email security in 2022 and the threats that should be on your radar in 2023. GET EBOOK>>
How do brand impersonation attacks work?
Typically, brand impersonation phishing attacks start with sending carefully designed emails that impersonate top brands. Sometimes these messages will create urgency by claiming that the victim’s account has been frozen and giving them a link to reset their password. Some emails even ask them to review their account or a document using a given link. When the unsuspecting victim clicks on the link, they land at a phishing website, which looks like a legitimate website, but is designed to harvest their login credentials. Once threat actors have access to the account, they can use it for all types of damaging activities, like stealing sensitive company data, transferring money to a fraudulent account, deploying ransomware or launching a business email compromise (BEC) scam.
Bad actors will be pushing harder than ever this holiday season. Yahoo predicts a 60% increase in online fraud during the 2022 holiday season as phishing and fraud attempts across all industries heat up for seasonal shopping. The U.S. Better Business Bureau (BBB) has also sounded the alarm about malvertising on social media, cautioning that ads for online exclusive deals from major brands can be dangerous. The BBB warns that these sites have a high risk of being fake and often mimic famous retail websites, cautioning shoppers to carefully ensure the authenticity of a website before entering any information no matter how good the deal sounds.

What worries security pros now & for 2023? The Kaseya Security Insights Report 2022 tells you. GET YOUR REPORT>>
Types of brand impersonation attacks
These types of brand impersonation phishing attacks are coming to flood employee inboxes unless companies take action to stop them.
- Email spoofing: In this brand impersonation attack, cybercriminals create fake email addresses that look identical to the ones that they want to impersonate to confuse their victim. For instance, attackers change a single character in the email address and alter the display name to make it seem like a legitimate email from a trusted source.
- Brand Hijacking: It is one of the common impersonation techniques to spoof a company’s email domain to impersonate the organization or one of its employees. Also, known as brandjacking, the attack is getting a lot of attention the past few years.
An example of brand hijacking:
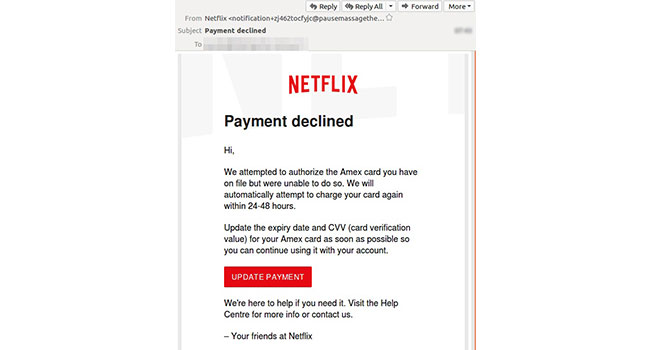
Source: Security Today
- Account takeover (ATO): This attack is especially nasty. In ATO, cybercriminals entice a user to provide their password through a phishing email, then lock the victim out and hijack their account. Bad actors will use these stolen accounts to perpetrate BEC or access a company’s systems for nefarious purposes.
- Executive Impersonation: In this type of cyberattack, attackers hack the accounts of a target company’s CEO or other top-level executives to steal their credentials. They use the compromised legitimate account to impersonate the CEO or executives to authorize fraudulent transactions and gain access to sensitive business information.
- Fake social media accounts: In this attack, cybercriminals create fake business social media accounts of brands or their employees by exactly copying all the data from the original account. Using these fake accounts, they reach out to the organization’s customers to steal their data and money.

Are you ready to stop ransomware? Find out with our 5 Steps to Ransomware Readiness infographic! GET IT>>
Ways to prevent brand impersonation attacks
According to the IBM Cyber Security Intelligence Index Report, human error is the primary reason for 95% of cyber security breaches. Security awareness training is the most effective and affordable weapon that businesses have against phishing and brand impersonation. An aware and educated employee can save organizations from significant loss of reputation and money. Companies that engage in regular security awareness training have 70% fewer security incidents. It pays for companies to send out reminders about smart holiday shopping and have employees brush up on brand impersonation, spoofing and phishing.
On the other side of the coin, organizations also need to keep an eye out for website or application infringement of their own sites, especially if they retail any goods or services that may be popular with holiday shoppers. Website or domain spoofing is one of the easiest and most popular ways for cybercriminals to facilitate a little holiday season brand impersonation quickly, and no company wants their name or site to be violated like that. Companies need to be alert and take active steps against brand spoofing to ensure that no one is using their brand name to tarnish their reputation or trick their customers.

See 10 reasons why Graphus is just better than other email security solutions. SEE THE LIST>>
Graphus takes human error out of the equation
Graphus is the world’s first automated phishing defense platform that seamlessly protects you from brand impersonation attacks. Using its patented AI technology, Graphus automatically detects phishing emails and safeguard your employees from falling into cybercriminals’ traps. It puts three layers of defense between a phishing email and your organization and prevents any phishing email from reaching an employee’s inbox. Graphus automatically monitors communication patterns between people, devices and networks to reveal untrustworthy emails, making it a simple, powerful, and cost-effective automated phishing defense solution for companies of all sizes.
Here are some of the features that make Graphus the best email security solution:
- Block sophisticated phishing messages before users see them.
- Put three layers of protection between employees and phishing email messages
- Seamlessly deploys to Microsoft 365 and Google Workspace via API, without big downloads or lengthy installs
- Provide intuitive administration and precise reporting to help you gain insights into the effectiveness of your security, level of risks, attack types and more
Book of demo of Graphus to start your email security journey.






