What Would an Incident Response Look Like for Me?

Does everyone on your team know what to do if disaster strikes? Incident response planning is often overlooked. After all, nobody wants to think about something as unpleasant as a cyberattack. But failing to think ahead can be devastating when disaster strikes, compounding the problem and potentially dealing a death blow to the impacted business. An estimated 60% of businesses that are hit with a cyberattack shutter within 6 months. Strong, smooth incident response is a key factor in determining if a company joins that club.
This post is adapted in part from our NEW Creating an Incident Response Playbook. DOWNLOAD IT NOW>>
Creating a Plan Isn’t as Hard as You Think
If you haven’t created an incident response plan for your business or your client’s business, you’re also leaving money and advantages on the table at a time when every point in your favor counts.
- An eye-popping 94% of executives say their firms have experienced a business-impacting cyber-attack or compromise within the past 12 months
- Only 39% of organizations with a formal, tested incident response plan experienced an incident at all, compared to 62% of those who didn’t have a plan.
- Having a tested incident response plan can save 35% of the cost of an incident
You can develop effective incident response plans fairly painlessly. The US National Institute of Standards and Technology (NIST) has a series of free publications available with incident response recommendations complete with an industry-standard incident response framework and implementation guide.
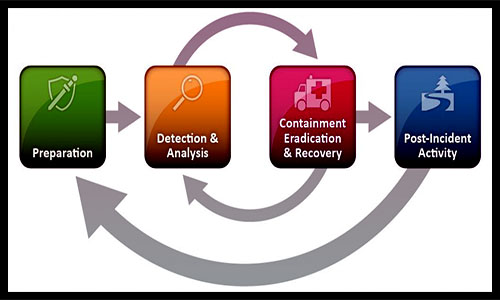
The NIST Response Cycle
The most prominent set of industry best practices for cybersecurity incident response is maintained by the US National Institute of Standards and Technology (NIST). The agency’s four-part incident response cycle is the model that most organizations use to create their own incident response. The NIST incident response cycle divides the incident response cycle into four distinct steps that take you from start to finish when handling any cybersecurity incident.
See how to avoid cybercriminal sharks in Phishing 101. DOWNLOAD IT>>
How Would This Work for My Business?
Here is how creating an incident response plan might work for your business based on the NIST Incident response Cycle. In this example, we’ll be looking at a response to a ransomware attack. To give you a concrete example of a response to a risk that your business faces daily.
Preparation
This may be the hardest step because it’s easy to rush through it. But this is also the most important step. Having the right people on the team will make all of the difference.
Create a team
If something like ransomware infects your systems, who gets the first call? Who do they call? Who has access to the things that are needed to triage the problem? Who needs to be informed?
In an emergency, you need to be able to answer those questions quickly and definitively. That’s why every business should start its incident response planning with establishing a Computer Security Incident Response Team (CSIRT) and setting the hierarchy, responsibilities and capabilities of that team in stone. In an emergency, you don’t have time to waste on deciding who does what.
Establish a protocol
How exactly will everyone be informed and get their instructions on how to handle the incident – and who is empowered to make hard decisions? This is where your decision matrix fits into your plan.
The framework of your plan can use any criteria you choose and be customized for your business. The most important part of this step is to establish the parameters of your planning framework, then use that framework to create your response plan for every incident. Consistency in format and layout for each plan will make it easy for your CSRIT to execute it during a disaster, enabling them to stay focused on the next two steps.
Detection and Analysis
The first step to fixing the problem (and mitigating the damage) is to figure out the problem. To continue with the ransomware scenario, this is the step where your security personnel finds the cause, extent, and location of the damage, then report it to the CSRIT.
What is the problem? In our scenario, it’s ransomware, so we’ll be starting at the most likely point of infection, email accounts, because most ransomware attacks start with a phishing email (like 90% of cybersecurity threats do).
What caused the problem? Let’s say an employee got caught by a phishing email and downloaded a PDF that contained ransomware. An estimated 94% of ransomware arrives at businesses via email
Where did the damage start and where has it spread? We determine that the ransomware originated from that employee’s email account. That then enables us to see where else it may have migrated by doing some basic forensics.
Containment, Eradication and Recovery
Containment
Example Ransomware Incident Questions: Is the data or network encrypted? Can we isolate the infection or impacted systems? What systems and data did the affected computer have access to? Can this incident be handled remotely?
In this step, your CSRIT will decide how to minimize the damage from the incident and keep the business running. This may also be a place where you’ll need to know what can be sacrificed if necessary.
Eradication
Example Ransomware Incident Questions: Can we remove the ransomware? Can we restore our data and systems from backup? What will we do if we can’t?
This is the step where your CSRIT decides what the most expedient and effective way of eliminating the problem is for your business. Every business had unique needs and capabilities, so this step may vary dependent on the systems and data affected. You may want to include multiple options that account for each variable that affects the choices that your team will encounter here.
Recovery
Example Ransomware Incident Questions: Where are the backups? Who has access to the systems and software that you need to get back to work? How do we fix the damage?
This is the step that requires the most pre-planning. Restoring your business to full operations may be impossible without secure backup and recovery options for your data. You may also need to bring in specialists to handle PR, technical and legal issues, especially if your industry or location means that you’re dealing with complicated compliance issues or extensive reputation damage.
Post-Incident Activity
Example Ransomware Incident Questions: Is there reporting to be filed with the government or industry officials? What went right with our incident response plan? What went wrong? How can your team improve their performance next time? Do we need to adjust our plan?
After the incident ends and you’ve started getting back to normal, an after-action report is a must. It pays to immediately analyze your incident response plan, your CSRIT ’s performance and your decision matrix. Finding weaknesses in the plan or process and addressing them immediately will help you create a better plan for the future.
Then, spend some time determining what you can do to reduce the chance of this being a problem for your business in the future. In our ransomware scenario, a staffer unleashed a ransomware nightmare because they were fooled into interacting with a phishing email. How can you prevent that from happening again?
AI is the secret weapon you’re looking for to boost business email security. SEE WHY>>
Stop Security Breaches Before They Start
Phishing is today’s most common vector for a cyberattack. Automated, AI-powered protection for email boxes is the best way to guard against phishing risk – an automated security solution like Graphus catches and kills 40% more phishing threats than conventional security or a SEG. The ideal choice to combat the flood of dangerous phishing email heading for every business, Graphus layers security for more protection with three powerful shields.
- TrustGraph uses more than 50 separate data points to analyze incoming messages completely before allowing them to pass into employee inboxes. TrustGraph also learns from each analysis it completes, adding that information to its knowledge base to continually refine your protection and keep learning without human intervention.
- EmployeeShield adds a bright, noticeable box to messages that could be dangerous, notifying staffers of unexpected communications that may be undesirable and empowering staffers to report that message with one click for administrator inspection.
- Phish911 enables employees to instantly report any suspicious message that they receive. When an employee reports a problem, the email in question isn’t just removed from that employee’s inbox — it is removed from everyone’s inbox and automatically quarantined for administrator review.






