Why You Should Be Worried About This Devastating (& Growing) Cyber Threat
In recent times, cybersecurity worries have been hogging the attention at the decision table in many companies and rightfully so. Even slight negligence can wreak havoc on the business and jeopardize its future. On top of that, the increased volumes and sophistication of business email comprise (BEC) attacks are adding to the worries of IT teams within organizations. BEC scams have quickly evolved as cybercriminals’ weapon of choice to make serious money, especially as ransomware operations become tricky thanks to law enforcement scrutiny.

Follow the path business takes to a ransomware disaster in The Ransomware Road to Ruin. DOWNLOAD IT NOW>>
BEC attacks are rising fast
BEC scams utilize legitimate (or freshly stolen) email accounts from a trusted business to fraudulently acquire money, personal information, financial details, payments, credit card numbers and other data from another firm. These scams also target companies that use wire transfers, foreign suppliers and other invoice transactions. One of the biggest reasons for the proliferation of these attacks right now is that the cybercrime-as-a-service market is booming and cyberattacks like BEC and can be largely automated or farmed out to phishing specialists.
Increased law enforcement scrutiny around ransomware has also driven cybercrime groups that have in the past been primarily devoted to ransomware attacks to turn their attention to BEC operations. It’s not a challenge for a ransomware gang to quickly pivot to BEC because the two cyberattacks share enough functional similarities that a major ransomware gang can utilize most of its existing resources to get the job done. That has been a contributing factor to the surge in BEC that businesses have been enduring. The percentage of businesses that had suffered a BEC attack grew by 18% last year. The pace is only escalating as BEC attacks doubled between Q1 and Q2 2022.
Explore today’s biggest threats & what’s next in The State of Email Security 2022 GET IT>>
Avoid the potentially fatal financial blow that is BEC
A BEC attack leads to losses that are both financial and reputational. Once your business suffers a BEC attack, its impact can devastate your present and future revenue while also damaging your brand and business relationships. According to The Ponemon 2021 Cost of Phishing Study, the financial impact of phishing attacks quadrupled over the past six years, with the average cost rising to $14.8 million per year for U.S. companies in 2021, compared with $3.8 million in 2015.
BEC devastated U.S. businesses in 2021. In the U.S. Federal Bureau of Investigation Internet Crime Complaint Center (FBI IC3) 2021 report, BEC attacks topped the charts for financial damages to businesses Complainants to IC3 suffered a whopping $2,395,953,296 in losses in 2021, 28% higher than 2020’s record total of $1,866,642,107.
Cybercrimes in 2021 by Victim Loss Total
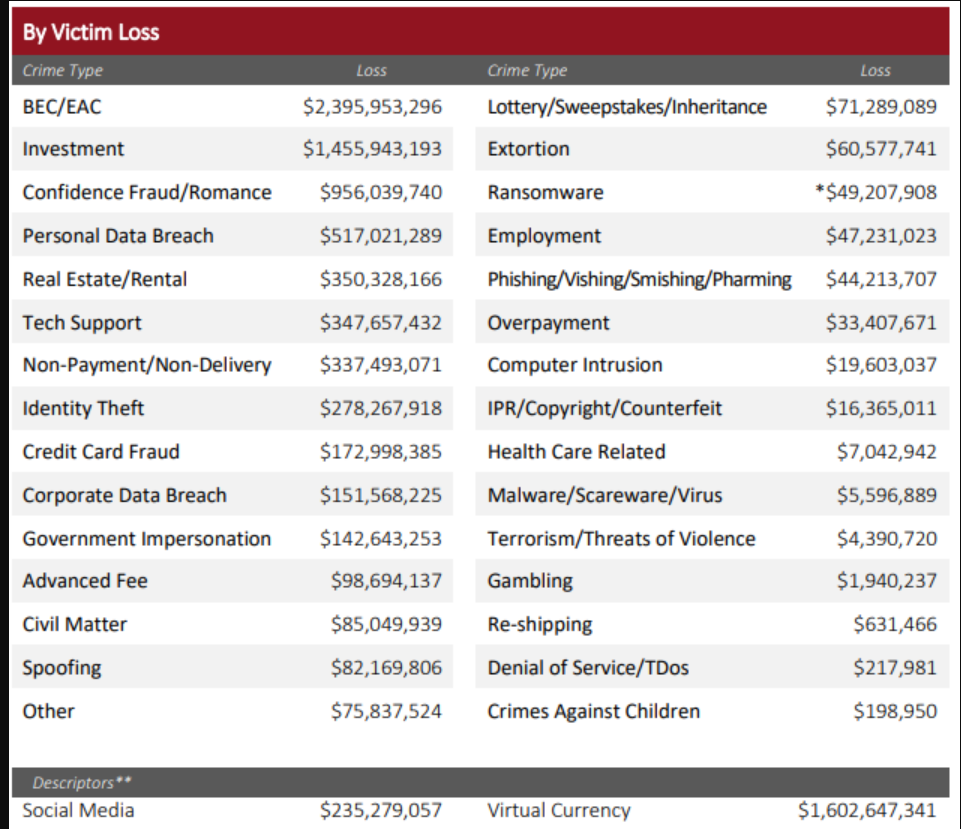
Source: FBI IC3

Get the guide that helps you detect & defeat dangerous BEC attacks to keep your company out of trouble! DOWNLOAD IT>>
Learn from these real BEC examples
To launch a BEC attack, cybercriminals often use a standard phishing scheme and then lend it authority by impersonating a trusted and often high-ranking individual associated with the targeted organization. In one particular instance, the cybercriminals launched a BEC attack on a prominent sports company by sending phishing emails impersonating its CFO. The email included a forwarded message and an attached PDF file that claimed to be an insurance provider invoice, asking the recipient to make payment via an ACH electronic fund transfer. Fortunately, a savvy employee spotted the scam. While the sports company was able to foil this attack due to its awareness, many others do not. Here are some examples of successful BEC attacks.
- The Floyd County Schools were subjected to a cyberattack when its board of education wired $200,000 to a fraudulent bank account that they believed was associated with a roofing company. The school discovered the incident much later when the actual roofing company reached out to ask about the payment that the school system thought it had already made.
- Another incident of BEC attacks was reported by Microsoft, where a large-scale phishing campaign used adversary-in-the-middle (AiTM) phishing sites to attack roughly 10000 businesses in a month-long campaign. The cybercriminals stole passwords, hijacked a user’s sign-in session, and skipped the authentication process even if the user had enabled multifactor authentication (MFA). The attackers then used the stolen credentials and session cookies to access affected users’ mailboxes and perform follow-on BEC campaigns against other targets.
- The city of Portland, Oregon, was the victim of another incident where the cybercriminals used a BEC scheme to hijack one of the city employee’s email account to trick its employees into wiring $1.4 million into their accounts. The incident came to light when the city’s treasurer flagged the $1.4 million wire transfer as potentially fraudulent as the name of the account receiving the wire transfer failed to match Central City Concern’s bank account name.

AI is the secret weapon you’re looking for to boost business email security. SEE WHY>>
Stay alert to the warning signs of BEC
There is a popular saying in the cybersecurity realm, “A cybercriminal only has to be lucky once, while a defender has to be lucky every minute of every day.” That’s why you need to be on your toes all the time. In spite of the increased sophistication of BEC attacks, some red flags clearly indicate trouble. Oftentimes, these phishing emails have bad grammar, wrong punctuation, and spelling errors. BEC perpetrators also use spoofed or imitated email messages from a trusted sender as a lure. Be cautious about interacting with emails that look different than messages from a designated sender. Most importantly, always be wary if an unanticipated message requests immediate payment or a transfer of funds to a different address, like a private email account, or in a different way, like a cash app instead of a check. That’s a hallmark of BEC.

Are you ready to stop ransomware? Find out with our 5 Steps to Ransomware Readiness infographic! GET IT>>
Put a powerful guardian between BEC attacks and employees
The most effective way to foil a cyberattack is by proactively detecting and protecting any phishing email from reaching your employees. Automated, AI-driven email security can be your ally in protecting your business from the evolving threats of modern-day phishing attacks. Compared to the traditional standard email gateway (SEG), an automated solution provides 40% more security against all phishing attacks.
Graphus is the answer to all of your email security woes. With its triple-layered protection and patented AI technology, Graphus automatically monitors communication patterns between people, devices and networks to reveal untrustworthy emails, making it a simple, powerful, and cost-effective automated phishing defense solution for companies of all sizes. Graphus identifies and blocks a wide variety of threats including social engineering and zero-day attacks to keep businesses safe from even the most sophisticated phishing threats.
- Graphus blocks sophisticated phishing messages before users see them.
- Puts 3 layers of protection between employees and dangerous email messages.
- Seamlessly deploys to Microsoft 365 and Google Workspace via API, without big downloads or lengthy installs.
- Provides intuitive reporting to help you gain insights into the effectiveness of your security, level of risks, attack types, and more
- Book a demo of Graphus






