Is DMARC fully protecting your organization from email-based attacks?

Have you implemented DMARC but still experiencing successful cyber attacks? We’ve previously written about why DMARC is not enough when it comes to protecting your organization. This post is going to provide an example of where DMARC failed but Graphus® detected a malicious attack.
As discussed in our previous post, DMARC is an email-validation system designed to detect and prevent email spoofing. It is intended to combat certain techniques often used in phishing and email spam, such as emails with forged sender addresses that appear to originate from legitimate organizations. It is built on top of two existing mechanisms, Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM).
DMARC builds trust into the “From” header field in an email by aligning it to the SPF and DKIM domain fields (also known as “Identifier Alignment“). Domain owners can set up DMARC policies telling the recipient servers to take certain actions – for example, if SPF and DKIM for a specific email don’t pass, it can reject the email.
Setting up DMARC isn’t an easy task and is a necessary one as it helps with the domain reputation of an organization. However, it’s not going to fully protect your organization from email-based attacks.
Graphus® detects attacks that circumvent DMARC
Graphus® protects your organization and employees from attacks such as:
- If a malicious sender has created a domain very similar to another domain and enabled SPF/DKIM/DMARC, then the recipient server will consider emails from this domain to be legitimate. These messages will land in users Inboxes. Graphus®, however has the specific capability to detect similar sounding domains and will mark these emails to be suspicious, generate a real-time alert, can apply a warning banner, and could even auto-quarantine the message.
- If the email account of a sender your organization has communicated with in the past is compromised and malicious messages are sent from their account, then even though SPF/DKIM/DMARC are setup for this domain, these messages will land in the Inbox of a recipient. Graphus®, however can detect these messages by leveraging our TrustGraph®.
- If malicious senders have setup valid domains and configured SPF/DKIM/DMARC properly, then the recipient servers will consider emails from these domains to be legitimate. Graphus®, however can mark these emails as suspicious or malicious based on its robust detection algorithms that takes into consideration multiple criteria to create a trust rating.
- Graphus® also has the capability of identifying all communicating domains which do not have SPF/DKIM/DMARC setup properly. These domains can be notified to take preventive actions to ensure their reputation stays intact.
Graphus® superior detection capabilities powered by the TrustGraph®
Here is an real example of a message Graphus® detected that SPF/DKIM/DMARC let through.
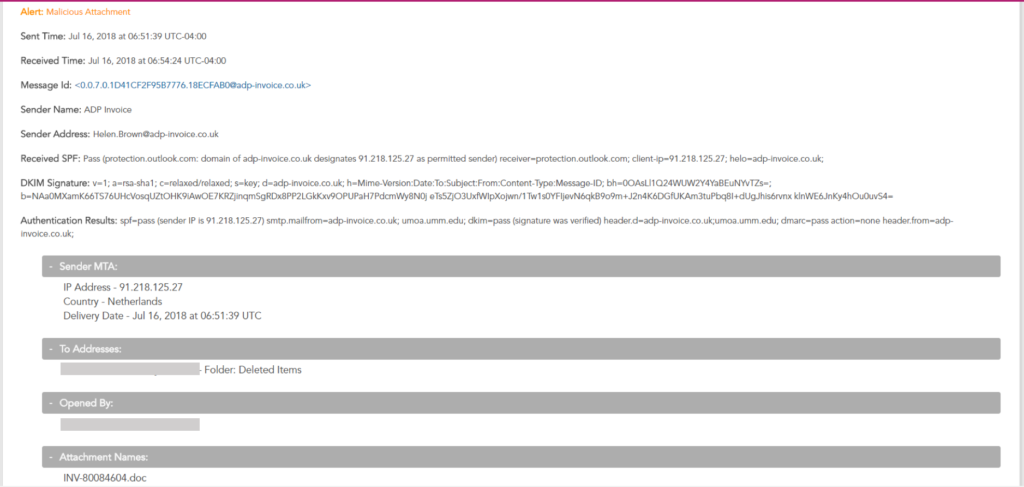
As you can see, SPF, DKIM, and DMARC passed however this message contained a malicious attachment. Graphus® was able to automatically detect this message, generate a real-time alert for the customer, and auto-quarantine the message within a matter of seconds.
Graphus® integrates with Office 365 and G Suite APIs making for a tight connection. This solid integration allows for an effortless activation with nothing to download, configure, or install as well as in-depth insights and extremely accurate detection capabilities.






