New Report on Spear Phishing and Social Engineering Risks and Best Practices

People are your weakest link. That is what the data tell us about cybersecurity risk today. Every day there are more great tools to protect your network, endpoints and applications. Still others expose threat intelligence, more accurately report intrusion attempts and even identify nefarious behavior by insiders. Cyber criminals know this and are fueling the arms race with ever more sophisticated methods of attack.
The Rise of Asymmetric Attacks on Your Employees
However, hackers also are very effectively engaging in asymmetric attacks that have little to do with technology and instead exploit human psychology. That is why companies report that 65% of social engineering and spear phishing attacks lead to credential compromise. Most of your cybersecurity investments do nothing to protect you from these attacks.
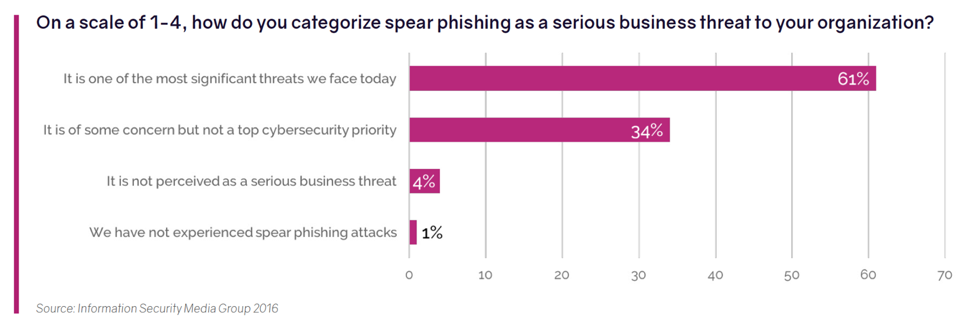
Employees are inadvertently ushering cyber attackers into your networks, data bases and financial accounts because they are trying to be responsive to seemingly legitimate requests. The more service-oriented and responsive your company culture, the greater your risk. That is why 61% of company IT departments report that spear phishing is among the most significant threats faced by businesses today.
15-Page Report on Spear Phishing and Social Engineering Tactics
Graphus released a 15-page report today that breaks down the primary tactics used in spear phishing and social engineering attacks along with the types of damages incurred by victims and common strategies for defense. The table of contents includes:
- Market Data on the rise of spear phishing and social engineering
- Definitions and examples of phishing, spear phishing, whaling and social engineering
- The 5 agonies of cyber attack victims (what types of damages are sustained)
- How spear phishing impacts your customers and business partners
- The strengths and limitations of phishing training for employees
- Filling the big gaps where DMARC, DKIM and SPF offer no protection
- How to employ graph theory and machine learning to automate protection
We look forward to hearing your feedback on the analysis and answering questions you have about protecting your organization from spear phishing and social engineering attacks.






