Ransomware Grew 750 Percent in 2016 and Most of It Was Delivered Through Spear Phishing

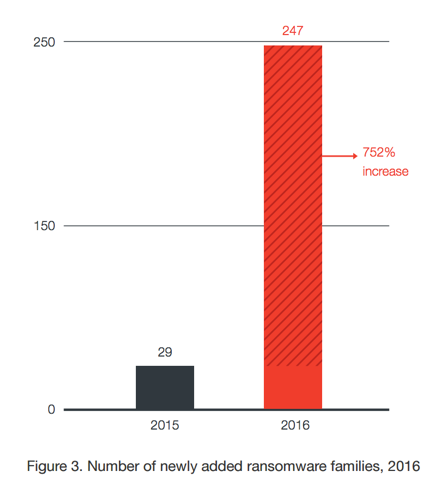
Trend Micro reported last month that Ransomware attacks increased 752% in 2016. Ransomware families grew to 247 last year from just 29 in 2015. Why the rapid growth? Well, ransomware attacks work and attackers are getting paid. The report suggests that ransomware is now a $1 billion business.
The trend has continued into 2017. The WannaCry ransomware attack in May of this year resulted in 45,000 attacks spread across 99 countries on a single day according to Kaspersky Labs. It is widely regarded as the largest single ransomware attack in history.
Spear Phishing Delivers the Ransomware
The questions related to ransomware attacks are not just about what it does, but includes how it gets distributed in the first place. Trend Micro has an answer for that question too. The company reports that 79% of ransomware attacks originate through spam. It is a business email compromise (BEC) attack that relies on phishing and spear phishing techniques to become implanted on a computer and then wreak havoc across an enterprise network.
Because healthcare is such a common target, Modern Medicine magazine focused on explaining ransomware in a recent issue.
“The ransomware usually infiltrates a healthcare organization through an email to an employee. The email typically looks legitimate and trustworthy, along with a link to click…Once the employee clicks the link, a piece of software is downloaded to their computer. The software will encrypt files on the user’s local drive and any network drive that can be gleaned from the computer. Next, a notice appears on the computer screen that encryption has occurred and that the files are no longer available to the healthcare organization. Instructions are also provided on how to pay a ransom to recover all compromised files and operating systems.”
This is a good explanation of the process for activating malware within an organization in most industries. Again you saw that social engineering through email is the most common attack vector. The WannaCry ransomware incident was also delivered through email.
How to Protect Yourself from Ransomware
The first way to protect yourself from ransomware attacks is to prevent yourself from becoming the victim of a spear phishing attack. If you can prevent business email compromise, then you eliminate nearly 80% of all attacks. Some people have experimented with training programs which have shown some success but still lead to 25-35% of phishing attacks successfully executing on their objective. Graphus provides an automated solution that has been shown to protect against spear phishing.
You should also ensure that your vulnerability patches are up-to-date and that you back up data on a regular basis so restore points can get you back online faster. Ransomware is a big problem today because it is successful. Tools to stop phishing attacks, identify spear phishing emails and patch vulnerabilities are focused on preventing ransomware before it becomes implanted in your organization. Back-ups help you recover after an attack. So, what is your plan to prevent a ransomware incident in your organization?






