Spear Phishing & Social Engineering
People are your weakest cybersecurity link. What are you going to do about it?
TABLE OF CONTENTS
- INTRODUCTION
- DEFINING THE ATTACKS
- THE FIVE AGONIES OF CYBER ATTACKS
- IT’S NOT JUST ABOUT YOU
- TRAINING IS NECESSARY BUT INSUFFICIENT
- AUTOMATED PROTECTION AGAINST SOCIAL ENGINEERING ATTACKS
- WHAT SHOULD YOU DO?
PEOPLE ARE YOUR WEAKEST LINK - AND ATTACKERS KNOW IT
What is your biggest cybersecurity risk? A hacker with sophisticated network penetration tools? A SQL-injection into a web application that you host? A DDoS attack? None of the above.
Symantec reports that “91% of cyber attacks start with a spear phishing email.” And companies are noticing. In a 2016 survey by Information Security Media Group (ISMG) 61% of companies reported that spear phishing was “one of the most significant threats we face today.”
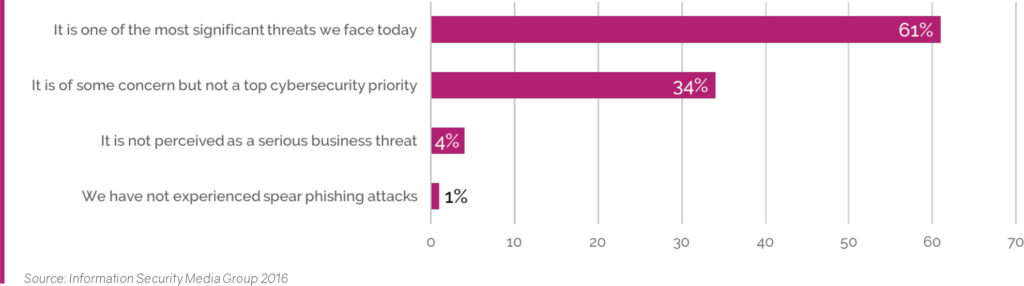
Another survey by CyberEdge Group produced a similar finding. Spear phishing represented the second highest concern category for IT security teams. And, we know from other data that the most frequent delivery method of the top concern, Malware, is spear phishing. After years of implementing more robust protections for the network perimeter, it is the messages we willingly allow inside our network that are causing the biggest risk.
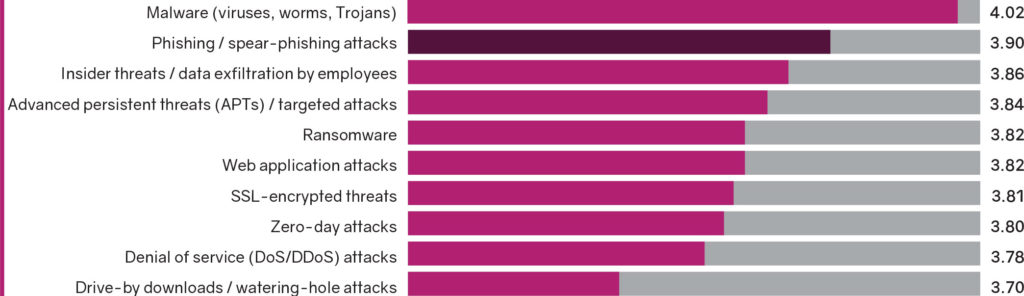
TWO OF EVERY THREE SOCIAL ENGINEERING ATTACKS SUCCEED
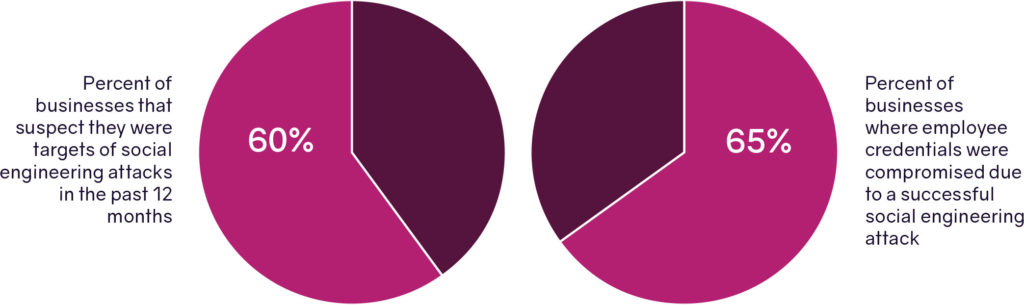
These concerns are supported by an increasing corpus of industry data. For example, spear phishing is often considered a subset of the Social Engineering category of attacks. The ISMG survey also found that 60% of businesses suspected they were targets of social engineering attacks in the previous 12 months. Of those companies, 65% confirmed that employee credentials were compromised as a result of the incidents. This is much higher than even traditional phishing compromise success rates, which are also notoriously successful. The costs for business are tremendous. FBI data shows the average loss per incident is over $130,000.
Spear phishing and social engineering prey on human psychology and its many weaknesses. These attacks aren’t going away. In fact, they are increasing because they work. How many people simply trust an attachment presumably sent by a friend? How many employees will respond quickly to an email from their boss that contains an urgent request? How often do these quick reactions violate known processes or simple common sense? The answer to these questions is many, many and very often.
You can lock down your networks, but you can’t lock down the ability to communicate with the outside world. These personal communications represent your biggest cyber risk today and cyber criminals know it.
WHAT YOU WILL LEARN FROM THIS ANALYSIS
- Definitions for phishing, spear phishing, whaling and social engineering.
- The five agonies of successful cyber attacks.
- The effect on customers and business partners
- The benefits and limitations of spear-phishing and social engineering training
- How new technologies are enabling automated protection.
We look forward to your feedback on the content. Feel free to send any questions you have about the source material and cyber defense strategies to mailto:[email protected]
DEFINING THE ATTACKS
Phishing, Spear Phishing and Social Engineering are often used interchangeably and incorrectly. They are different, but some of the confusion arises when a cyber attack employs more than one technique. For example, social engineering may be used in concert with spear phishing. Malware may also be the malicious payload delivered by spear phishing email. Proofpoint found that 99.7% of documents used in attachment-based campaigns relied on social engineering and macros. The following are common definitions and examples to help clarify the differences between the terms.
PHISHING
Traditional phishing scams cast a wide net in hopes of catching a few unwary victims. Typically, the target will receive an email that looks legitimate and warns the person that they need to login to a website to perform a certain action. The email will contain a link to what looks like a legitimate website and the victim will be asked to enter their account details. Once entered the cyber criminal will use that information to steal, commit fraud or obtain even more valuable information. The attack strategy is to contact a large volume of potential victims in hopes of identifying a handful that will click-through and fall for the ruse.
Phishing attacks generally involve a malicious attachment or a malicious link to a compromised website. Ars Technica reported on several phishing-initiated ransomware attacks in 2016 against hospitals.
“March has not been a good month for hospital IT, Staff at Methodist Hospital in Henderson, Kentucky paid a ransom to restore the hospital’s systems, reportedly of $17,000— though sources familiar with the episode say the hospital paid much more. And in California, two hospitals operated by Prime Healthcare Management, Inc. were forced to shut down systems. The Prime ransomware attack also caused disruptions of service at several other hospitals and at affiliate care providers as shared systems were taken offline…The Methodist Hospital and Prime Healthcare ransomware attacks came in via ‘phishing’ e-mails.”
SPEAR PHISHING
By contrast, spear phishing is about small numbers of contacts that deliver a high conversion rate. Spear phishers obtain private information by researching the background of individuals and companies on social media, corporate websites and other publicly available information. Cyber criminals use that targeted information to convince the victim to perform a task or share information. A recent article from the Berks County, Pennsylvania local news site provides a good example.
“Weidenhammer has been victim of a spear phishing event that has resulted in the transfer of 100 percent of our 2016 W-2’s to an unknown party,” the founder of Weidenhammer Systems Corporation informed employees in 2017. “You should assume your Social Security number, your home address, your 2016 earnings and all of the tax withholding that would appear on a W-2 has been compromised,”
“The perpetrators have already begun to use the information to file fraudulent federal and state income tax returns for 2016, apply for home equity loans and open/defraud credit card accounts,” John Weidenhammer said
This example illustrates how quickly a spear phishing scam can defraud company employees. However, the more typical danger is directly to the company finances or intellectual property. The Infosec Institute recorded details of another spear phishing attack on Ubiquiti Networks in 2015.
“The potential destructiveness of a spear phishing attack for a business is shown clearly in the case of Ubiquiti Networks Inc., an American network technology company for service providers and enterprises. In June of 2015, the company lost $46.7 Million because of a spear phishing e-mail. A report by the U.S. Securities and Exchange Commission shows that the attack was carried through ‘employee impersonation and fraudulent requests from an outside entity targeting the Company’s finance department.’”
WHALING
This is a newer term and is simply a spear phishing attack targeting senior executives, the whales. An example from 2016 involves the high profile social media networking company Snap, known for its popular Snapchat app. Digital Guardian offered this summary of the attack.
“In early 2016, the social media app Snapchat fell victim to a whaling attack when a high-ranking employee was emailed by a cybercriminal impersonating the CEO and was fooled into revealing employee payroll information.”
A 2015 example targeted Mattel, the world-famous manufacturer of Barbie and other toys. CBS News reported:
“The email seemed unremarkable: a routine request by Mattel’s chief executive for a new vendor payment to China…The finance executive who got the note was naturally eager to please her new boss. She double-checked protocol. Fund transfers required approval from two high-ranking managers. She qualified and so did the CEO…Satisfied, the executive wired over $3 million to the Bank of Wenzhou, in China. Hours later, she mentioned the payment to Sinclair. But he hadn’t made any such request.”
SOCIAL ENGINEERING
While phishing schemes typically rely on email, attachments and webpages to capture private data, social engineering might use these, the phone or any number of different methods. Social engineering involves psychologically manipulating people into divulging information or taking inappropriate actions. Very often victims have no idea they have done something wrong until the fraud is later exposed. Like spear phishing, social engineering attacks are highly targeted at a small number of potential victims. A USA Today article outlines one such attack technique in 2016.
“In one of the more recent incarnations of this scam, the criminals posing as lawyers contact targeted company executives claiming that they are handling important, confidential or extremely time-sensitive matters and use psychological pressure to trick the company executive into wiring the funds to the scammers.”
Another example comes courtesy of Smartfile. It outlines an attack on the FBI using a simple social engineering technique initiated through a telephone call.
’So, I called [the helpdesk] up, told them I was new and I didn’t understand how to get past [the portal],’ the hacker told Motherboard. ‘They asked if I had a token code, I said no, they said that’s fine—just use our one. I clicked on it and I had full access to the computer.’
“Soon after that, 20,000 FBI and 9,000 Department of Homeland Security records were released to the public. The hacker accessed employees’ names and even credit card information. Using the IBM 2015 cost per record breach standard ($170 per record based on malicious activity), that’s nearly $5 million dollars lost during a 2-minute phone conversation. It was probably higher, given the amount of credit card data and the as-yet-unknown implications of the national security data that was accessed.”
Another example comes courtesy of Smartfile. It outlines an attack on the FBI using a simple social engineering technique initiated through a telephone call.
’So, I called [the helpdesk] up, told them I was new and I didn’t understand how to get past [the portal],’ the hacker told Motherboard. ‘They asked if I had a token code, I said no, they said that’s fine—just use our one. I clicked on it and I had full access to the computer.’
“Soon after that, 20,000 FBI and 9,000 Department of Homeland Security records were released to the public. The hacker accessed employees’ names and even credit card information. Using the IBM 2015 cost per record breach standard ($170 per record based on malicious activity), that’s nearly $5 million dollars lost during a 2-minute phone conversation. It was probably higher, given the amount of credit card data and the as-yet-unknown implications of the national security data that was accessed.”
All of these techniques can lead to account credentials compromise, use of malicious links or malware as part of the attacks. Many information security breaches involve multiple tools, techniques and procedures (TTP) as the industry saying goes. But, most of them start with a simple email. Phishing, spear phishing, whaling and social engineering are typically used as points of entry to initiate an attack or as points of escalation to move the attack into scenarios where more valuable information can be obtained or more damaging actions initiated.
THE COSTS ARE BIGGER THAN YOU THINK – THE FIVE AGONIES OF CYBER ATTACKS
Now that we know the types of attacks, it is useful to understand the types of damages that companies regularly incur via cyber crime. FBI data shows that social engineering attacks cost companies an average of $130,000 with damages climbing into the millions of dollars for many companies. However, any victim of a cyber attack will tell you that these losses are only a portion of the damage sustained. There are up to “Five Agonies” inflicted by any successful cyber attack.
- Direct financial loss
- Recovery cost
- Lost productivity
- Business disruption
- Reputation damage
HOW MANY AGONIES WILL YOU ENDURE?
You can guarantee that every successful cyber attack, no matter how minor, will result in some lost productivity. Someone must resolve the issue, make a change or deal with a delay. If you catch the attack early, lost productivity might be your only damage. Attacks that are caught late often involve multiple agonies that make the incident even harder to absorb.
This means that every successful attack includes between one and five of the agonies. In our list, we order them based on what people think about first when confronting the risk of cyber attack. The reality is that the severity of impact is often in the exact opposite order. While the direct financial loss and recovery costs are often paid for in the quarter they occur, business disruption and reputation damage may undermine company finances for months or years.
The Five Agonies represent what you are protecting the organization against. The cyber criminals may simply want your money or secrets, but the damage typically extends well beyond cash.
DIRECT FINANCIAL LOSS
The most prominent agony is direct financial loss. This is what drives the captivating news headlines. It is typically easily measured and often relates directly to the cyber criminal’s take from the attack. Social engineering and phishing scams are highly effective. They have even spawned the new Whaling technique discussed earlier. Damages tend to range from a low end of $25,000 to multi-million dollar losses.
RECOVERY COST
Calculating recovery cost is also relatively straightforward. The organization paid an incident response team to clean up after an attack. New software is purchased to resolve the compromise and protect against future intrusions. Credit monitoring is purchased for affected customers. There are invoices you can add up. This is the second most common cost after productivity loss. Many incidents don’t actually result in stealing company funds or ransoming data but result in data loss that leads to business secrets or customer information being auctioned to bidders on the dark web.
PRODUCTIVITY LOSS
Every cyber attack involves some productivity loss. Often, it is substantial and hard to fully document. Countless meetings, employee updates, customer communications, and other activities extend well beyond the IT and security teams. Every minute employees spend on discussing or taking steps related to a cybersecurity breach represents time not directed towards operating the business. This is a substantial cost that is rarely calculated.
BUSINESS DISRUPTION
Productivity loss measures the impact on people’s time and attention. Business disruption is about impacts to your customers and supply chain. If your equipment can’t operate, you may need to run overtime shifts to make up for delays. If you can’t ship product from your warehouse, you may miss your quarterly revenue target or spend time expediting shipments to make up for the delays. Anxious customers may switch to a supplier that can provide competing products immediately. After a breach, your bank and insurance company may ask to audit your security practices. Security incidents that disrupt business operations can have long lasting impact.
REPUTATION DAMAGE
It is very difficult to regain trust from customers and suppliers after you have had a significant cybersecurity incident, especially if it was well publicized. Is your trust in a supplier shaken when they have been breached and potentially lost confidential information about your business? It is a natural reaction and can undermine a company’s reputation for years.
If you or your boss ever needed motivation to beef up your cybersecurity, this list should help. The alternative is to find your motivation after you have suffered through one or more of the five agonies. However, you need to think more broadly than the four virtual walls of your organization. Companies are more connected to customers and suppliers than ever before and their practices can impact your security just as your practices impact theirs.
IT’S NOT JUST ABOUT YOU
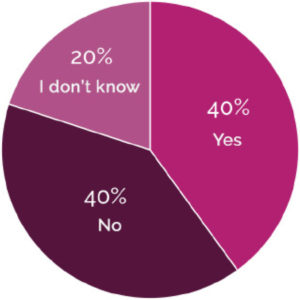
There is an added challenge that we must all face. Your risks are not constrained by the boundaries of your organization. The ISMG study referenced earlier also found that 40% of companies were aware of their organization or brand identity being used to spear phish customers or partners. This risk falls into that reputation damage category, but it may also lead to direct financial costs if weaknesses in your security lead to a successful spear phishing attack at a customer or supplier.
Are you aware of situations where your organization or brand identity has been used in attempts to spear phish your customers or partners?
The logical extension of this is that you are not simply subject to risk of your own employees falling for a social engineering scam. If your customers or business partners are compromised that information can be used to spear phish your organization. There is a cascading set of consequences when these attacks are successful. And, they are often successful as we have shown.
Marsh & McLennan Agency talked about just such a compromise in a 2015 blog post: “Another common method is when a criminal poses as an employee of a vendor, and requests changes to the vendor’s bank account for all future payments. If a company official is fooled by the ‘vendor,’ the criminals will divert funds from the company until the ruse is discovered.” Who do you think pays for this loss?
TRAINING IS NECESSARY BUT INSUFFICIENT
An analysis of Ponemon Institute data by Womba Security found that employee training on phishing can reduce damages by $1.8 million. The finding is based on Ponemon data suggesting that the annual cost of phishing for companies is $3.8 million and 47.75% of that can be offset by phishing training programs. The total estimated losses will vary across companies, but it is reasonable to assume the relative benefits of phishing training are significant.
A 2016 study at Germany’s Friedrich-Alexander University (FAU) in conjunction with data from Verizon suggests how much impact training can have. The FAU study found that 56% of people clicked on malicious links in emails despite that fact that 78% were aware of the risks of clicking unknown links. Aware is not trained. It is just aware. Verizon DBIR data revealed that about 12% of employees clicked on links in 2016 after training. That represents a 79% reduction in phishing success rates and strong recommendation for training programs.
However, it still means that one out of every eight phishing emails are getting through and we know that spear phishing is at least five times more effective. There is also concern that training may not have a lasting impact as the rate of clicks on phishing emails actually increased between 2015 and 2016.
THE NEED FOR AUTOMATED PROTECTION
The need for more automated protection was addressed in a 2014 Bank Infosecurity interview with Vanderbilt’s Eric Johnson and its relevance seems even more pertinent today.
“While many organizations rely on employee training to help mitigate the risks of spear phishing, such efforts are generally ineffective, says Eric Johnson of Vanderbilt University, who explains why a technical solution might be more effective. Vanderbilt conducted a study that concluded ‘training exercises are not going to move the needle a lot,’ Johnson says.
“That really puts the ball back into the technical court,’ he says. ‘That is, how can we protect users from ever being able to make a decision on these things either by ensuring they never receive the e-mail to begin with, warning them appropriately in the e-mail, or by catching them as they click and preventing that connection from occurring?”
The question for IT teams is clear. Training can help, but it clearly is insufficient. The attacks are coming more frequently and with higher success rates. You can lock down your networks, but you can’t lock down the ability of your people to communicate with the outside world. These personal communications represent every company’s biggest cyber risk today. Thankfully, there are now tools that can automatically detect social engineering attacks and risk factors and keep your organization safe. People are now your weakest cybersecurity link, but combining automation, machine learning and graph theory can help.
AUTOMATED PROTECTION AGAINST SOCIAL ENGINEERING ATTACKS
Graphus has stepped into this gap in cybersecurity protection. Using graph theory, machine learning and big data algorithms to identify trusted relationships between your employees and the people they communicate with, Graphus virtually eliminates the threat of spear phishing and social engineering attacks delivered through email. The solution automatically identifies and eliminates known and newly identified dangers. We know that about 65% of spear phishing attacks are successful even after employees have been trained to identify phishing emails. People are easily fooled. Graphus is not.
GOING BEYOND DMARC, DKIM AND SPF
G Suite and Office 365 both offer basic spam protection. Other software providers rely on DMARC, DKIM and SPF. When implemented properly, DMARC, DKIM and SPF technologies can protect domain owners against one scenario of domain name spoofing commonly used by cyber criminals. That protection provides some value. However, these technologies also leave open large gaps that spear phishing and social engineering swim right through.
First, some definitions. DMARC stands for Domain-based Message Authentication, Reporting and Conformance. It is an email authentication protocol that uses DKIM and SPF protocols. DKIM is Domain Keys Identified Mail and is email authentication specifically designed to detect domain spoofing. It enables the email receiver to check that an email that claims to come from a specific domain was authorized by that domain owner. SPF is Sender Policy Framework and is an email validation system that enables receiving email exchanges to validate that an incoming mail originated from IP Address they have authorized as trusted. Email spoofing is displaying an email header that appears to come from a one source, usually a trusted source, but actually originates elsewhere, typically an untrusted or unknown source.
WHERE DMARC, DKIM AND SPF HELP AND FALL SHORT
Targeted attacks from social engineering or spear phishing can be broadly sorted into two categories that either:
- Spoof an identity known to the recipient
- Use identity not known to the recipient
In the first category where a known identity is spoofed, you will see three common scenarios for the header FROM: “friendly_name” :
- FROM address is spoofed exactly: user@domain
- Only the “friendly_name” is spoofed: “friendly_name”
- A known name is used along with a similar looking domain to spoof the domain: name@similar_looking_domain
The second category takes a different approach
- Any domain can be used: the sender is not spoofing a known identity and may or may not be spoofing the actual domain name.
If DMARC is implemented to either quarantine or reject emails that fail SPF or DKIM then it will protect the recipient targeted in an attack from scenario (a). It is important to note that if a domain implements SPF and/or DKIM but not DMARC or has implemented DMARC only in monitoring mode, then the recipient targeted using scenario (a) is not protected. This is a common mistake. However, even if you are properly protected from scenario (a), DMARC doesn’t protect recipients targeted using scenarios (b), (c) or (d).
DMARC.org addresses these issues directly in its FAQs. It states that, “DMARC is designed to protect against direct domain spoofing.” That is scenario (a) from above. However, it goes on to say that scenarios (b), (c) and (d) are not addressed:
Does DMARC block all types of phishing attacks? No. DMARC is only designed to protect against direct domain spoofing. If the owners/operators of example.com use DMARC to protect that domain, it would have no effect on otherdomain.com or example.net (notice the “.net” vs. “.com”).
While impersonating a given domain is a common method used for phishing and other malicious activities, there are other attack vectors that DMARC does not address. For example, DMARC does not address cousin domain attacks (i.e. sending from a domain that looks like the target being abused - e.g. exampl3. com vs. example.com), or display name abuse (i.e. modifying the “From” field to look as if it comes from the target being abused).
FILLING THE SPEAR PHISHING PROTECTION GAPS
The question for IT security and business owners today is how to get past these deficiencies. Graphus was built based on twenty years of expertise working with DNS, email, threat intelligence, graph theory, machine learning and big data algorithms. The intersection of these fields led to the development of a TrustGraph® that can be built programmatically for each email domain in realtime. Patterns of interaction between people, computing end points, networks and threats provide insight into what communications can be trusted and which exhibit anomalous behavior.
The learnings were packaged into a simple, powerful, automated system that anyone can use because it works automatically on your behalf. Employees are protected from malicious emails before scammers can fool them with manipulation techniques based on human psychology. Graphus provides a dashboard that shows exactly what is going on, where you are being attacked and how to investigate further. However, most users rarely consult the dashboard because Graphus protects you automatically.
WHAT SHOULD YOU DO?
The FBI reported 17,642 victims of business email compromise (BEC) between October 2013 and February 2016. The reported cost of these attacks was $2.3 billion giving us an average loss of $130,000 per incident. But, readers of this report know that is only part of the cost since direct financial loss is only one of five agonies these businesses sustained.
You can lock down your network, but can you really keep your people from communicating with customers, suppliers and partners? Unlikely. That means we can secure all the windows with the latest cybersecurity tools, while cyber attacks come through the front door courtesy of unsuspecting employees responding to emails that they believe are legitimate. This is where Graphus can help. These personal communications represent your biggest cyber risk today.
So go ahead and invest in phishing training and DMARC. There is value in both. However, also recognize that these solutions do not provide total protection. In fact, they only provide protection at the margins. Graphus fills in the gap in your cybersecurity protection by eliminating broad risks associated with spear phishing and social engineering. Our guarantee to eliminate 99% of spear phishing and social engineering communications offers IT leaders and business owners peace of mind that they are protected from the most common types of cyber attacks.
“We were looking for a solution for social engineering threats that went beyond employee training. I was pleasantly surprised when Graphus caught an extremely sophisticated attack involving URL link to malware hosted at someone’s Google drive” Surendra Goel - Urgently CTO & Chairman










