Verizon Says Phishing Still Drives 90% of Cybersecurity Breaches
Verizon’s analysis of 1600 cybersecurity incidents and 800 breaches found that phishing was involved in 90% of successful attacks. Despite years of phishing awareness training, employees are still getting fooled. Verizon even included a section in this year’s Data Breaches Investigations Report (DBIR) called, “Attack the Humans.” Why? Humans are your weakest link. You can create a new rule to block an automated web application server attack, but you can’t eliminate human nature.
Who is Targeted? Everyone.
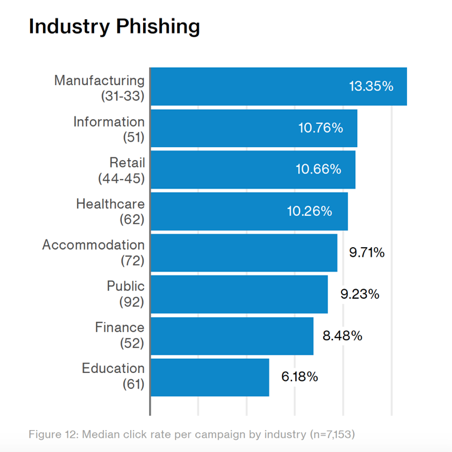
Social engineering attacks used to be someone else’s problem or at least that was what many people thought. Today, it is everyone’s problem. Verizon found that every industry was highly susceptible to these attacks. While employees at manufacturers were most likely to become victims, every industry had a significant percentage. When you consider that you only need one employee to be fooled by one email of the many they may receive in a single year, the percentages add up to that 60%+ likelihood of a company becoming a victim annually.
Many Employees Fall Victim Multiple Times
Beyond looking at breach data, Verizon also evaluated phishing success rates in a controlled study. To do this, Verizon gathered a base of three million users across 2,280 organizations. They then ran 14,000 campaigns. The results were “7.3% of users across multiple data contributors were successfully phished – whether via a link or an opened attachment…about 15% of all unique users who fell victim once, also took the bait a second time.”
Social Engineering and Spear Phishing Are Costly to Victims

These simulated phishing attacks were generic and untargeted. However, the more tailored, spear phishing attacks have a success rate about nine times higher. While the data compiled by Verizon suggests 219,000 people out of three million employees fell for a generic phishing scam, you could expect that number to rise to 1.8 million for spear phishing or social engineering attacks. The latter approach takes more effort on behalf of the attacker, but the payoff can be large. “This year’s data features numerous incidents involving the impersonation of an executive to trick someone to transfer money (sometimes six-figure amounts) from the corporate accounts.”
Verizon calls these more sophisticated social engineering attacks pretexting and says these attacks are, “almost always targeted in nature (and hence over half of the marks were from the finance department), which means actors are doing their research to identify the right employee, and invent a believable story.” What is the favored method of initiating the attack? You guessed it. “Email was the top vector of communication, accounting for 88% of financial pretexting incidents.”
Human Firewalls Don’t Work. You Need Automated Protection
The data is consistent. Email attacks against humans circumvent your network protections and you only need one employee to take the bait and your company is compromised. Not only do 7% of employees fall for phishing attacks and over 60% fall for spear phishing, you can also see from the Verizon data that a significant number of employees will get fooled a second time. This is why automated protection is so important.
At Graphus, we support use of phishing training, tools like DMARC and SPF but we also recognize that these steps will still let large numbers of attacks bypass your defenses. This is where the Trust Graph implemented by Graphus provides an added layer of protection and detects social engineering attacks before an incident occurs. To learn more about the Graphus solution of automated spear phishing protection, click the button below.






