Graphus detects sophisticated SharePoint phishing attacks
Recently, Graphus has detected several Microsoft SharePoint attacks for our customers. These are newer attack types that are extremely well crafted and difficult to detect. What this looks like for the recipient is the following.
The recipient receives an email with a link to a SharePoint document. The attacks we’ve detected for our customers have been well crafted and look like a legitimate email requesting the recipient to login and review a SharePoint document.
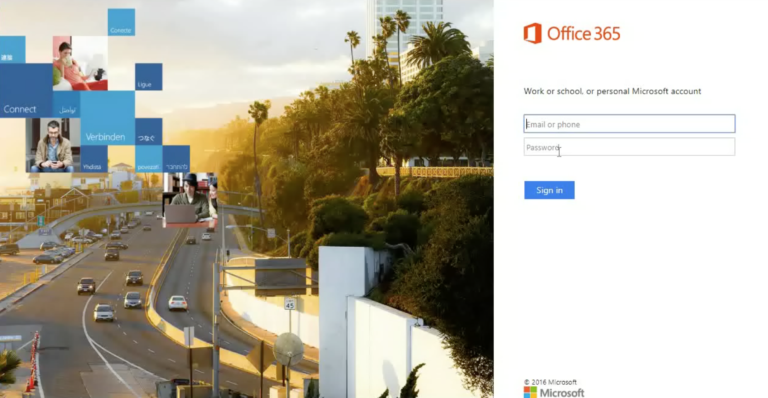
Once they click on the link within the email, they are taken to a page that looks like a Microsoft OneDrive login.

When the recipient clicks on “Review Document” it then takes them to a screen that asks them to login with multiple options.

When the recipient clicks on one of these options, it takes them to a login screen asking for their credentials.
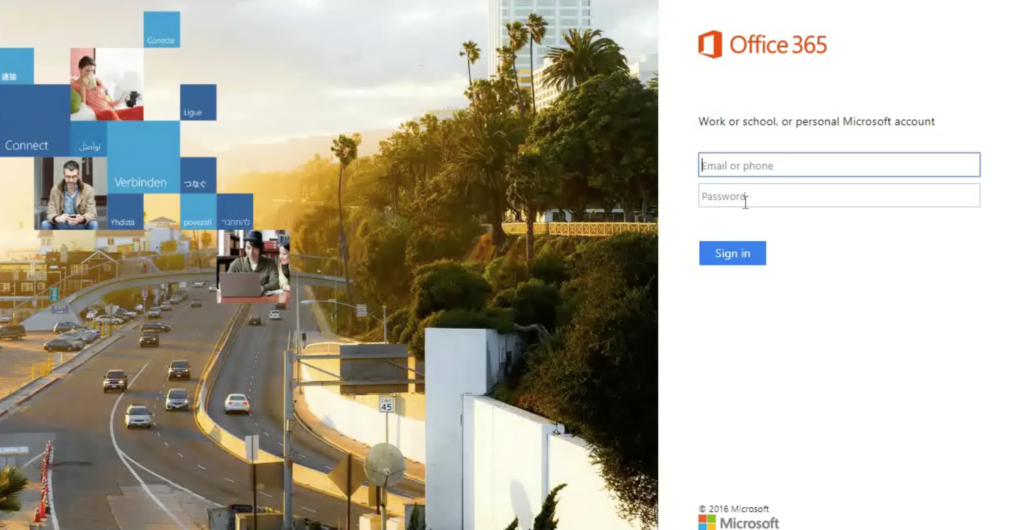
Having multiple ‘hops’ before reaching the page asking for credentials makes it difficult for standard detection solutions/methodologies.
How these attacks get past Office 365 & other security solutions
Microsoft Office 365 and other security products scan links in the emails looking for blacklisted or suspicious URLs. These cybercriminals are actually creating Office 365 accounts and enabling SharePoint, so when these emails come through, they have an actual SharePoint link/document. Because of this, Office 365 and other solutions do not identify this as a threat.
How Graphus® is able to detect these attacks
Graphus® is powered by a patented AI technology we call the TrustGraph®. This TrustGraph® is made up of various technologies and algorithms that allow it to learn, adapt, and continually get smarter. Each organization has their own unique attack surface, our TrustGraph® learns about your attack surface and adapts to specifically protect your organization from social engineering attacks. Graphus® also doesn’t rely on traditional threat intelligence. Instead we have developed proprietary and patented algorithms that can not only detect previous attack types but also new, and even zero-day attacks. When you combine this with the ability to detect suspicious or malicious links through multiple hops, it makes for a powerful solution.










