Hackers are constantly evolving their attack strategies. Are your security tools keeping up?
Graphus® detects new types of attacks on nearly a daily basis. From using Microsoft Forms, or voicemail phishing attacks, to leveraging SSL to get past other security tools or drive-by download phishing attacks that contain malware, bad actors are constantly evolving their attack strategies and companies of all sizes are being targeted – just ask Wipro.
Wipro, India’s third largest IT outsourcing company, was recently the victim of, what some are reporting as, a phishing attack that breached multiple employees email accounts. The hackers then launched attacks against roughly 11 of Wipro’s customers. This is exactly why IT and Managed Service Providers are massive targets for these hackers. The ability to breach one organization and easily expand to other businesses is a goldmine for them. The repercussions from this attack are just getting started and will impact Wipro for years to come, however, this is also why Graphus has found success working with IT and managed service providers.
Graphus® detects scams, business email compromise, spoofing, phishing, and malicious attacks everyday for our customers. These are highly targeted attacks that get past Office 365, GSuite, secure email gateways (SEGs), Microsoft ATP, and other technologies. With an attack like the one against Wipro, Graphus® would detect, alert, and auto quarantine the message instantly.
Organizations of all sizes are targeted every day and below are just a few examples of recent attack types Graphus® has detected for our customers.
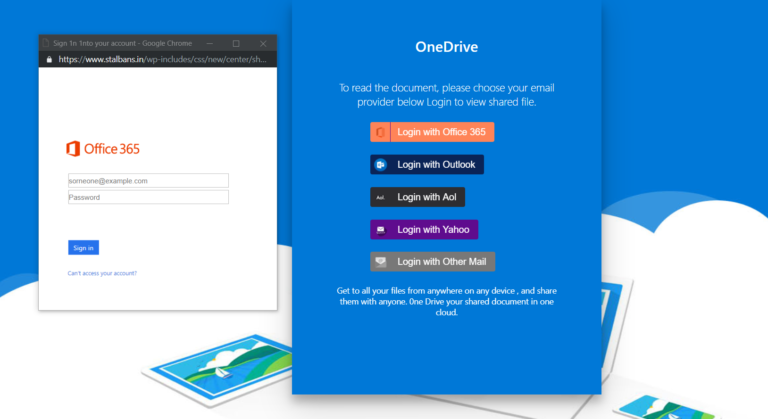
One of the more recent attacks Graphus® has detected is a phishing attack where hackers hide the phishing page if they detect that the phishing link was clicked from a Linux machine. Hackers know that typically phishing prevention software runs on Linux machines. On the other hand, Windows is still the most widely used operating system by users and is frequently paired with other Microsoft software offerings like OneDrive, SharePoint, or Office 365. If they detect that the phishing link was clicked from a Windows machine they would reveal the phishing site – like the one below, leaving the end users vulnerable to this attack.
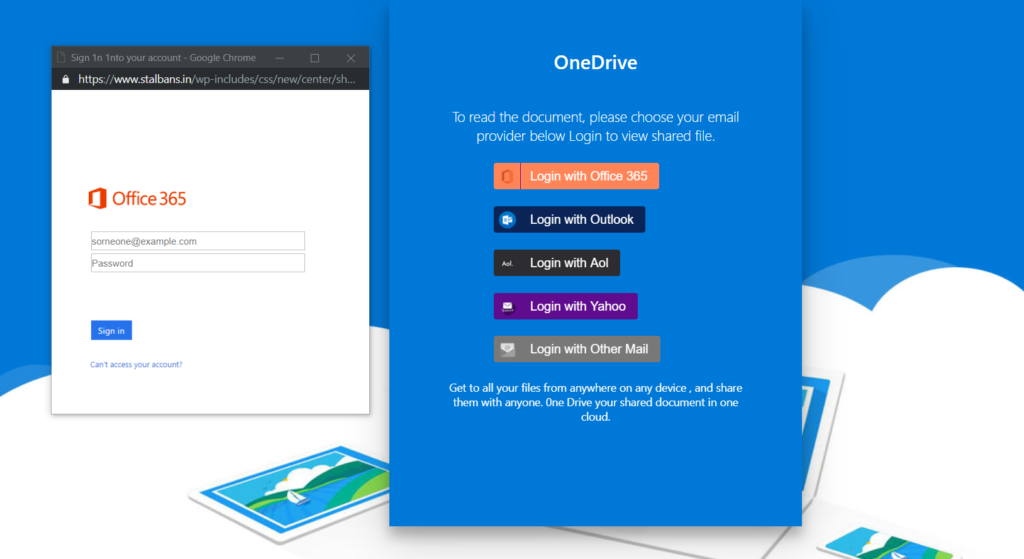
On top of this, the attacker has created multiple “login” pop ups depending on which Login button the recipient clicks on. For example, if they click on “Login with Outlook”, the screen below will be displayed.
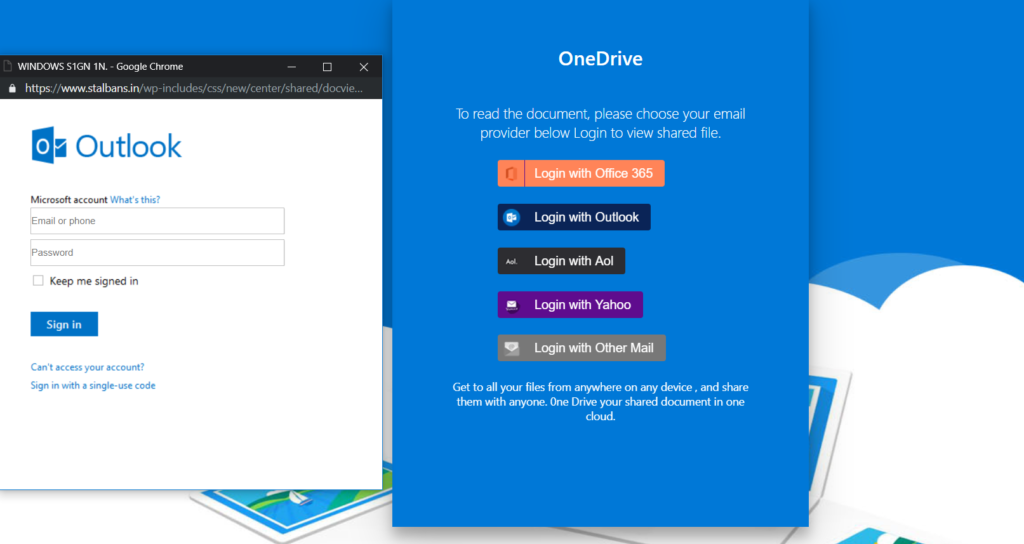
This increases the chances that someone, that may not use Office 365, will provide their login credentials and become the latest victim of a phishing attack.
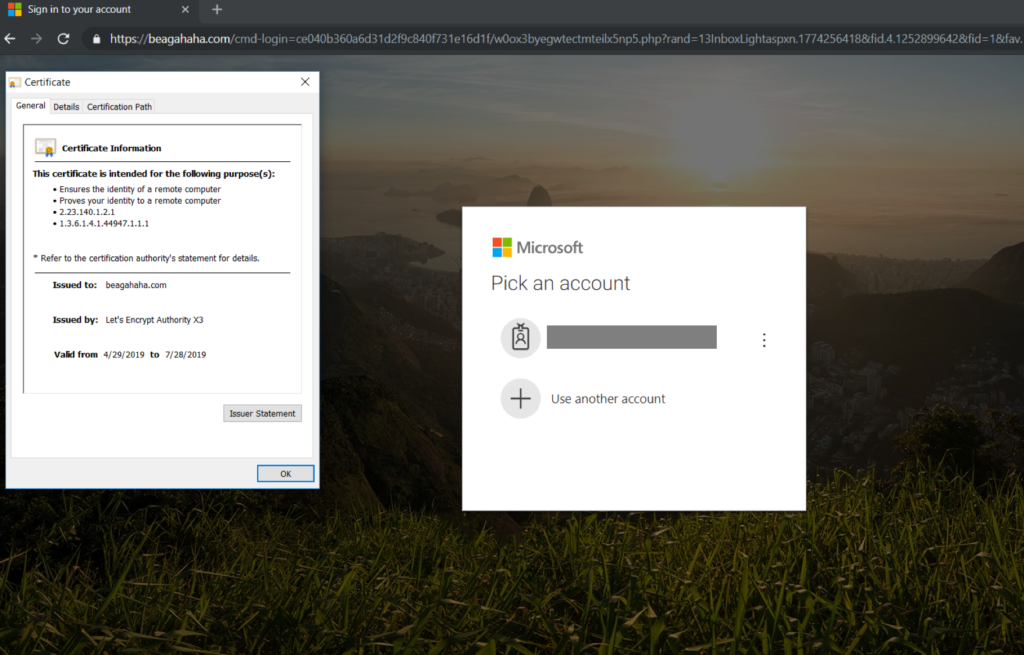
Another attack strategy we’ve seen on the rise are hackers using paid SSL certificates to appear safe and secure to the recipient(s). We’ve written about HTTPS attacks previously but the difference here is the hackers aren’t leveraging free/open-source SSL sources, they are actually paying for the SSL certificate. Like any business, if you are putting money into something, you want to see an ROI. For the hackers, they are paying for the SSL certificate and putting more time in developing the attack and therefore, want a strong return on their investment.
As for the recipients, seeing a website with HTTPS provides a sense of security but as the Authentic8 blog post HTTPS: Beware the False Sense of Security states, “HTTPS alone won’t protect you.” Some more sophisticated recipients will even click on the lock in the browser to see where the SSL certificate was procured. If it is a paid SSL certificate there can be a greater sense of trust from by recipient with regards to the site.
Graphus®, which is powered by our patented and proprietary AI technology – the TrustGraph®, doesn’t rely on traditional detection mechanisms. The bad actors know how these traditional solutions detect attacks and they are constantly evolving and finding new ways to go undetected and reach your employees. Don’t rely on traditional solutions to protect your business. Turn to Graphus® to protect your organization from targeted, zero-day attacks that get past traditional technologies.










