Sophisticated phishing attacks that leverage Google Drive

Detecting zero-day attacks is what Graphus® specializes in but what happens when the attack starts from a ‘trusted’ domain/URL? These can be nearly impossible to detect for most security solutions which means it is most likely making it into the inbox of your employees. But you may be thinking to yourself, “We provide phishing training for our employees.” This is a great point, however, when they see a familiar/trusted URL, such as drive.google.com, they tend to believe it is a safe message and provide credentials which result in your organization getting compromised.
So let’s see an example of what one of these phishing attacks looks like.
It first starts out with a well crafted email asking the recipient(s) to review a document. When the recipient(s) click on the link it takes them to a screen like this. Notice the secure Google Drive URL. This particular attack was detected by Graphus® on Monday September 10, 2018. As of now, Monday September 17, 2018, the URL was still active, and will probably remain that way because it’s hosted on Google Drive.

When the recipient clicks the “Continue to file” button, it then takes the recipient to a OneDrive login screen. You’ll notice in the URL that the attackers are still trying to use Google in the URL by typing “G00gle”. Recipients that quickly glance over this, may see “Google” and click one of the login buttons.
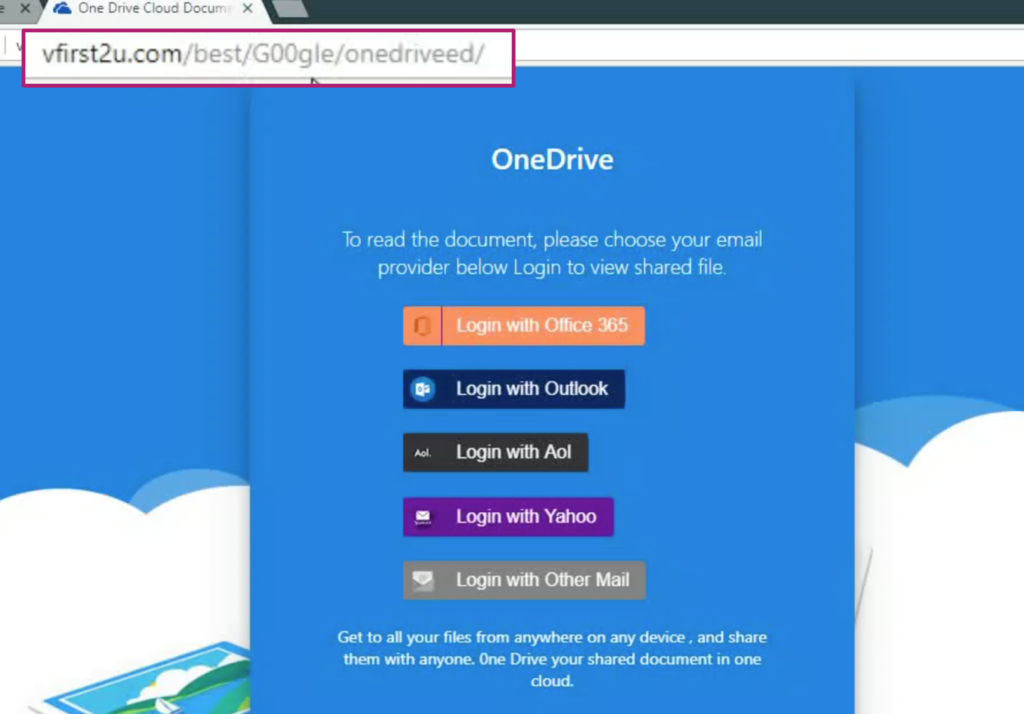
By clicking on any one of these buttons, a popup is displayed asking to enter credentials.
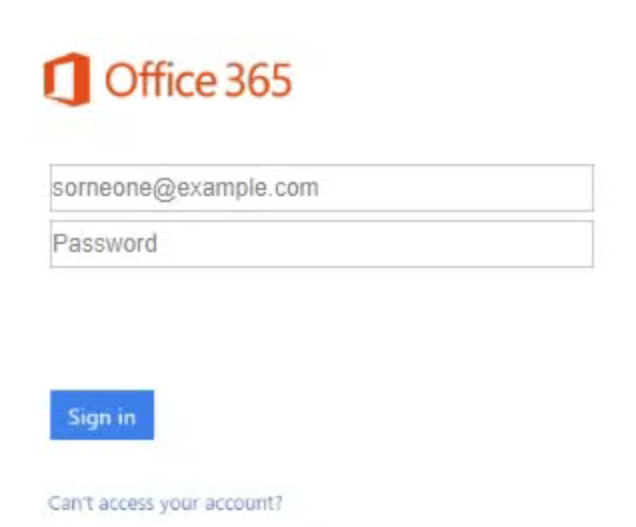
Hackers are successfully getting past security tools by having the phishing URL multiple hops away from the initial email. In this case, it was the 3rd URL a recipient got too before it asked for their credentials. This makes it difficult for these types of attacks to be detected.
We have seen a recent uptick in these types of attacks for both GSuite and Office 365 users. We’ve even seen this with our customers that have additional security tools in place on top of their existing GSuite and Office 365 security.
Because our customers have EmployeeShield™, they don’t have to rely solely on their employees guessing as to whether or not they should click or respond to a message. EmployeeShield™ provides them with a warning of a suspicious message and explicitly incorporates their feedback into automated workflow that instantaneously remediates threats, which drastically reduces the organizations risk.
Traditional security tools simply can’t keep up with highly sophisticated, zero-day attacks such as this one, but Graphus® can.










