How the Dun & Bradstreet Hack Increases Small Business Spear Phishing Risk

Dun & Bradstreet was hacked. So what? Lots of businesses are hacked. Why should I care about yet another cybersecurity breach? Well, this one very likely involves you personally. SC Magazine reported that:
“A Dun & Bradstreet 52GB database containing about 33.6 million records with very specific details about each of the people involved from job title to email address has been exposed.”
Hackers Turn Information into Context for Spear Phishing
Again, lots of emails have been made public through other hacks such as Yahoo. The difference with D&B is that it is business data which includes context useful to spear phishers. Troy Hunt reported the breach originally on his blog. He immediately recognized the risk this posed to companies:
“Take Wells Fargo, for example: this list makes it very easy to build a comprehensive picture of people and their roles. For example, there’s everyone in the C-suite, but that’s a pretty openly accessible set of data anyway. So go down a rung and you’ve got 45 Vice Presidents; Senior Vice Presidents, Assistant Vice Presidents, Executive Vice Presidents, all with names and email addresses alongside job titles.
“The value for very targeted spear phishing is enormous because you can carefully craft messages that refer to specific individuals of influence and their roles within the organisation. For example, sending a message on behalf of the “Vice President, Senior Private Banker” (her name is easily discoverable) to an accountant in the firm requesting an urgent transfer. Techniques such as whaling are made all the easier with this data and whilst that was always possible anyway, having so much of it in one place enables the automation of attacks across a broad range of organisations.”
We have seen from the many W-2 spear phishing scams that very little business information is actually required to trick employees into revealing sensitive company information. For example, Brian Krebs reported in 2016 on CEO impersonations and included this image from an email:
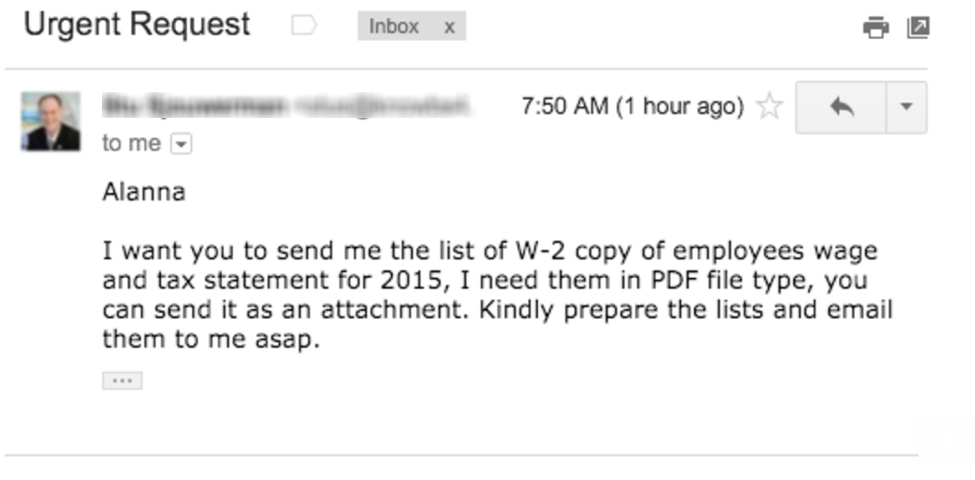
So what did the spear phisher need to know execute this attack? The names and contact information for the company CEO and someone in the finance or HR department that was likely to have access to the information. In the hands of a skilled spear phisher or social engineer, contact plus context equals compromise.
D&B Business Contact Database Had Much More Data
In fact, the database had much more information than just contact and context data. For example, Troy Hunt points out a reporter from ZDNet that was among the database records and agreed to have his record published for the blog.
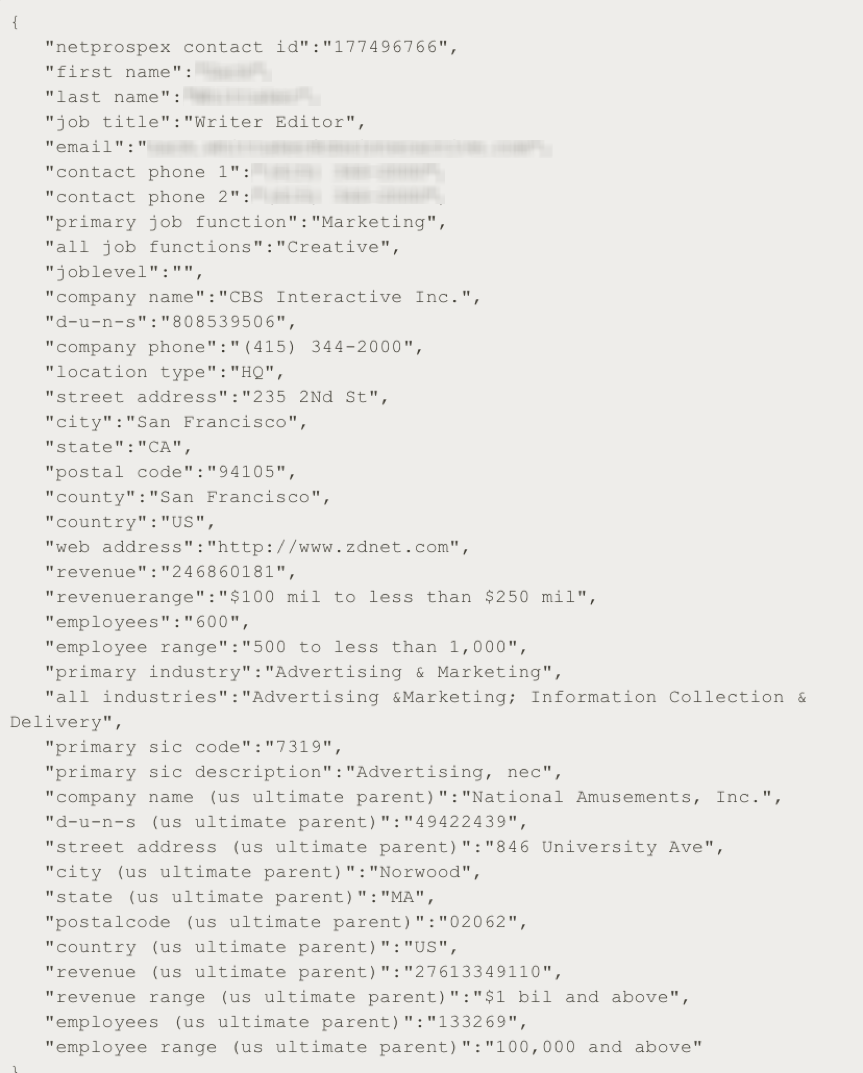
You can see that there is a great deal of information that can be used to quickly understand the type of company, the role of the individual and how they fit into the organization. Many if not all of the key elements of a successful spear phish are readily available. In addition to contact information, you can learn the number of employees of the company, its annual revenue and line of business.
Some people may incorrectly surmise that the D&B Netprospex database was only populated with information on large businesses. Many mid-sized and smaller businesses have DUNS numbers and their staff member information are included in the database. The example above, ZDNet is itself a mid-sized business. These contact databases can be used by anyone to target any type of business. And, the database was not limited to commercial enterprises. Many of the contacts work in government agencies.
How to Stop Spear Phishing?
We all know that phishing training can help. However, few people realize training only helps at most one-third of the time. The spear phishers are very effective which means the best approach is not to rely on your human employees to never be tricked by other devious humans, but instead to use automation to address the problem.
Graphus provides an automated solution that can be activated in about a minute and blocks spear phishing attacks. We cannot rely on humans to protect us from cyber crime as recent Verizon data reaffirms. Humans have become the weak link in our cybersecurity defenses. To learn more about Graphus, click the button below.










