Targeted drive-by malware attacks & how to handle them

Detecting and alerting messages that include malicious links (and attachments!) is nothing new for Graphus. Our product has been able to do this and auto-quarantine any emails carrying malware since it was released to the public.
Analyzing URLs and attachments in real-time and automatically removing threatening emails from the recipient(s) inbox has proven to be extremely valuable for our customers but attackers are constantly looking for ways to successfully circumvent the protections in place.
What is a drive-by malware attack?
More recently we’ve seen an increase in drive-by malware attacks across our customer base. These drive-by malware (or drive-by download) attacks are emails that include a link that causes the recipient to automatically downloads a malicious file – most of the time without the recipient knowing. Often times, drive-by malware is hosted on sites that have been hacked or exploited for propagating itself. The majority of the time these emails are received from senders not known to the recipient however, they can originate from trusted sources as well. A trusted sender that has been infected themselves can send drive-by malware attacks resulting in a greater likelihood that the recipient would click on the link.
Whether these threats are coming from a trusted source or not, drive-by malware attacks can be difficult to detect.
How does it work?
For an attacker to create a drive-by malware attack they must do the following:
- Create malicious content to perform the attack – which has become increasingly easier than ever before.
- Host the malicious content. This can be on their own server or on a compromised legitimate website which unknowingly distributes the attackers content.
- When the content in loaded by the client, the attacker will analyze the fingerprint of the client in order to tailor the code to exploit vulnerabilities specific to that client.
- Lastly, launch the drive-by malware attack. This can be done in a few ways but for the purpose of this blog post, we see these attacks carried out through email messages that have URLs that execute the download of a malicious file.
How can you protect against it?
Detecting drive-by malware attacks in an email is complex and not for the faint at heart. It requires all URLs to be analyzed in real-time for any download they might execute if clicked. If the URL does trigger a download then that download must be tested for malicious behavior. This requires extremely advanced detection techniques that scale to the volume and velocity of emails being received by an organization.
Graphus has developed such techniques that detect drive-by malware attacks and scale for large volume and velocity of email traffic. We are able to accomplish this by leveraging years of experience and utilizing big data algorithms and AI technologies resulting in a highly accurate and effective solution.
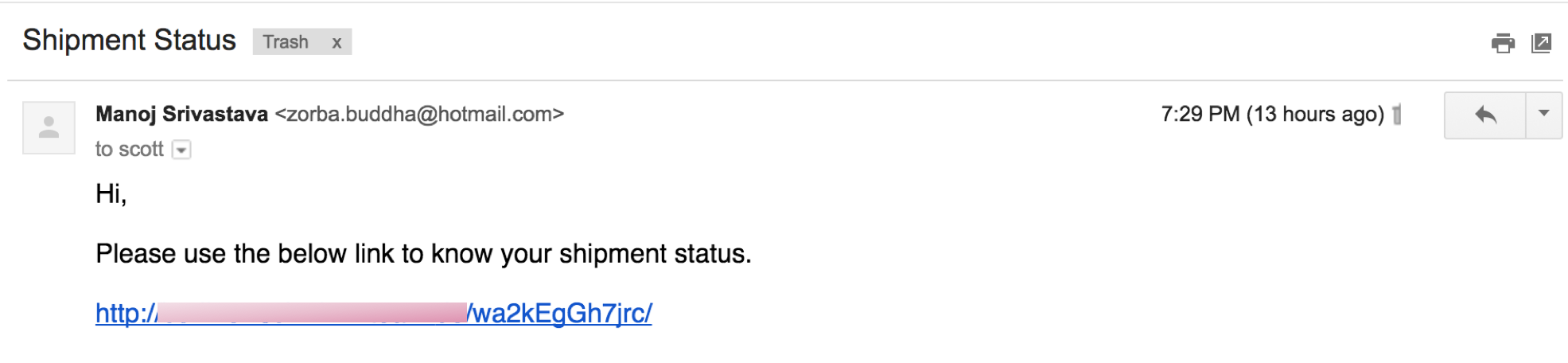
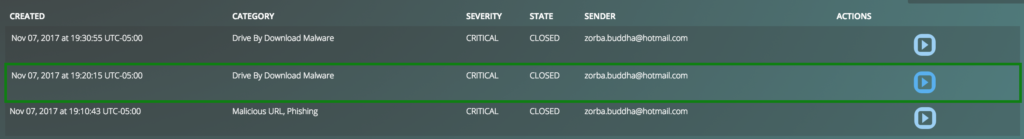
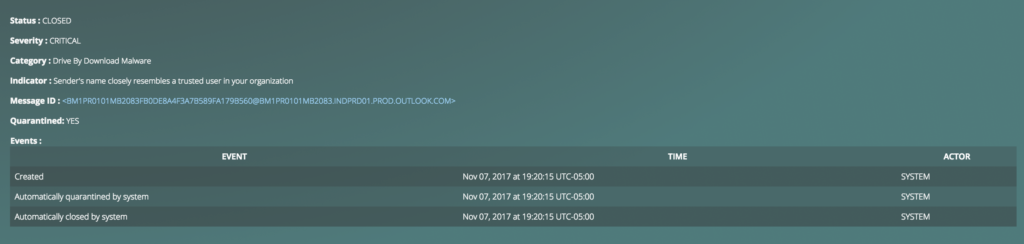
Below are the screenshots of the above email being capture and auto-quarantined in our system.
Interested in trying Graphus out? Click the button below.










