Graphus isn’t your grandpappy’s security solution
Attackers are taking advantage of our hurried up, multi-tasking, “I needed that yesterday!” way of life. Today, like many days, Graphus® detected a sophisticated, targeted phishing campaign against one of our clients. The attacker sent these phishing attacks first thing in the morning when people are just opening up their inboxes and are inundated with the number of messages waiting for their reply. As they are opening and responding to countless emails, there are phishing attacks sprinkled in with legitimate messages. Attackers take advantage of this time as employees are in a hurry and trying to respond to as many as they can before their first meeting.
We see this happen to organizations all the time and if they didn’t have Graphus®, they most likely would be yet another victim of a cyber attack and their IT or security department would have to spend hours, if not days or weeks, trying to recover.
Attacks consistently make it through traditional security solutions
Many of our clients’ traditional security solutions are not detecting these attacks which proves to be an enormous risk for their organization. Whether it’s Microsoft’s Advanced Threat Protection (ATP), legacy email gateway solutions, or other security technologies, these attackers have found creative ways to reach their employees.
For this particular attack, the hacker sent the message to 9 different individuals, many of whom were part of the senior leadership team, which is very typical.
The message tried to get them to sign in to what looked like their Microsoft account to steal their credentials.
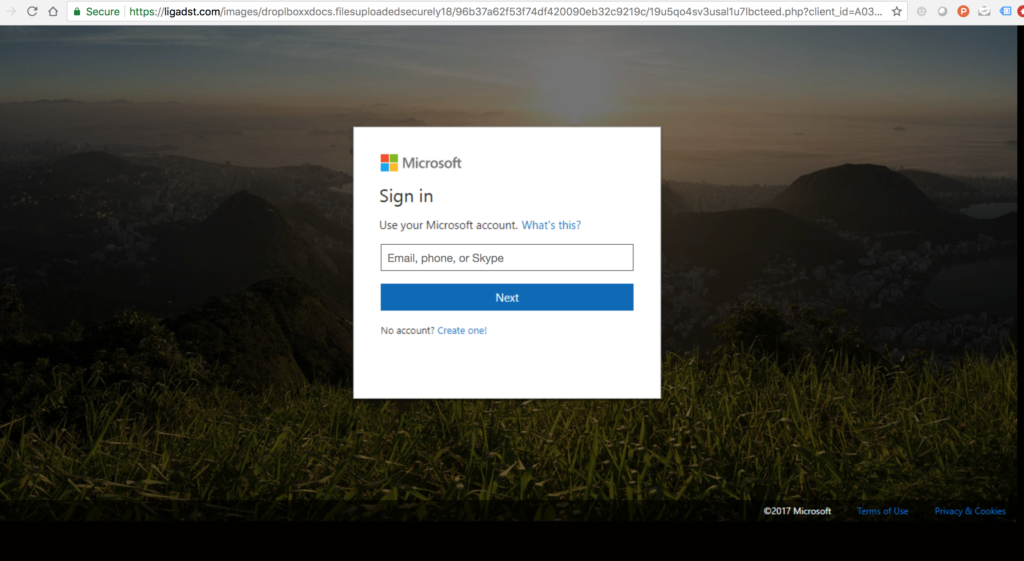
This seems like a straightforward attack and something that traditional security solutions should be able to easily detect, right? Well this attack had created a unique URL that had never been seen before, a zero-day attack, which allowed it to slip past more traditional technologies.
Not only did it slip past existing securities but these phishing URLs take several hours for browsers to realize it’s a phishing site. This attack took about 4+ hours for Google Chrome to realize it was a phishing URL. Some attacks take 24-48 hours before they are detected by a browser.
These 4+ hours when the phishing URL is going undetected are critical as the recipients could have opened and provided their credentials, giving the attacker access to sensitive information.
Graphus® isn’t your traditional security solution
Graphus® is the industry’s first automated social engineering defense platform. It provides immediate protection and peace of mind for Office 365 and G Suite users by automatically eliminating social engineering threats – spear phishing, phishing, and business email scams. We are able to detect sophisticated attacks because of our patented AI technology, the TrustGraph®.
For the attacks mentioned above, Graphus® detected these in real-time, generated an alert, applied a warning banner to the messages, and quarantined the messages from all inboxes. Again, these were zero-day attacks and each had a unique phishing URL. Graphus® saved our customer the headache of spending hours recovering from a successful phishing attack.
According to Accenture’s 2017 Cost of Cyber Crime Study, phishing and social engineering attacks cost U.S. companies, on average, $2.76M per successful attack. For a small investment in Graphus®, you could save your organization potentially millions of dollars a year dealing with phishing and social engineering attacks.
To learn more, click on the button below.










