One third of phishing attacks target financial services

According to Kaspersky Lab’s Spam and Phishing Q2 2018 report, over one third (35.7%) of all phishing attacks targeted financial services organizations – and the Fortune 500 aren’t the only targets. As we’ve written about before, small to medium sized financial service organizations are hit the hardest.
The FBI recently shared a private alert with banks stating, “Historic compromises have included small-to-medium size financial institutions, likely due to less robust implementation of cyber security controls, budgets, or third-party vendor vulnerabilities. The FBI expects the ubiquity of this activity to continue or possibly increase in the near future.” This was reported by Brian Krebs and referencing a potential upcoming global fraud scheme called “ATM cash-out”. This ATM cash-out is a plan hackers have devised to access ATMs around the world and fraudulently withdraw millions of dollars in a few hours. These cybercriminals are able to organize these types of attacks by hacking or phishing their way into a bank.
APWG recently reported that there was a 46% increase in phishing sites detected in Q1 of this year versus Q4 of last year. With phishing attacks on the rise, we expect to see more of these types of coordinated activities.
Example of a phishing attack against a financial services customer
We work with several financial services organizations here at Graphus and below is an example of a phishing attack one of our customers received that Graphus® detected.
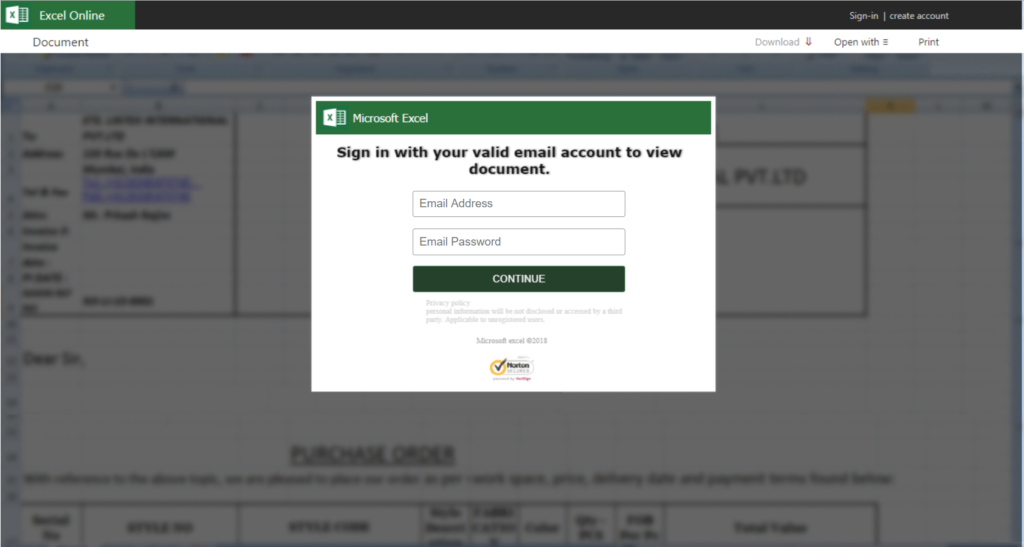
The email was sent to one of their executives and it included a message that said “Please review the purchase order details by clicking the link below”. For a busy executive, they may have quickly opened the email, clicked the link, saw this login page, and entered their credentials. If they did, the hacker would have been granted access to their account and been able to do any number of things to harm the organization or their customers.
Luckily for this organization they have Graphus® implemented. Our EmployeeShield™ feature was turned on, warning the recipient of this message and quarantining the alert before any damage was done.
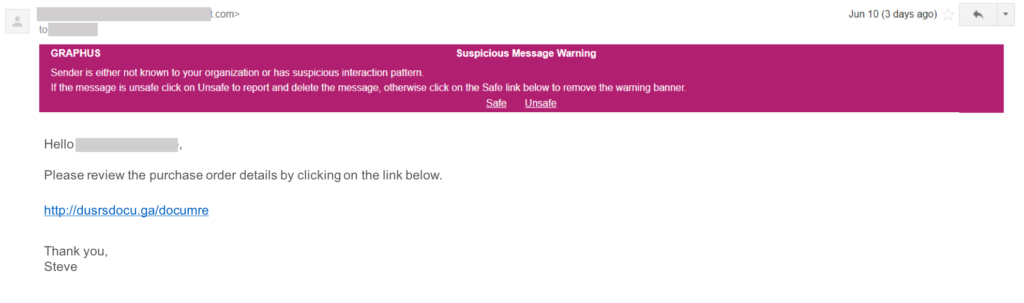
Hackers are betting on employees to be extremely busy and not always remember their phishing training (if they’ve had any training) and report suspicious messages to IT/Security. With Graphus®, it doesn’t matter if you’ve had phishing training or not. A warning banner is generated in real time to notify the recipient of suspicious messages and ask them to review and take appropriate action. Graphus® customer: 1; hackers: 0.










