3 Reasons Why Business Email Compromise is the Threat to Watch Today

What’s the biggest cyber threat that businesses face? It’s not ransomware, even though that tends to be the attack that gets all of the headlines. It’s business email compromise (BEC), and it’s the threat that everyone should be watching right now. Sometimes called email account compromise (EAC)— business email compromise is a scam that utilizes legitimate (or freshly stolen) email accounts from a trusted business to fraudulently acquire money, personal information, financial details, payments, credit card numbers and other data from another business. BEC leads to devastating losses that can destroy a business, and it’s on the rise right now.
AI is the secret weapon you’re looking for to boost business email security. SEE WHY>>
It’s 64x Worse Than Ransomware for Businesses
The Federal Bureau of Investigation (FBI) declared BEC a cyberattack that is 64x worse than ransomware for businesses. One reason for that is that BEC is the reigning champion of expensive cyberattacks, easily blowing other types of attack out of the water. In the FBI Internet Crime Complaint Center (IC3) 2021 Internet Crime Report, analysts outlined the stark reality of just how fast BEC is growing and how dangerous it has become. Reported losses from business email compromise attacks increased by 65% between July 2019 and December 2021. Between June 2016 and July 2019, the FBI’s Internet Crime Complaint Center (IC3) received 241,206 complaints from domestic and international victims, amounting to $43 billion in total exposed dollar loss.
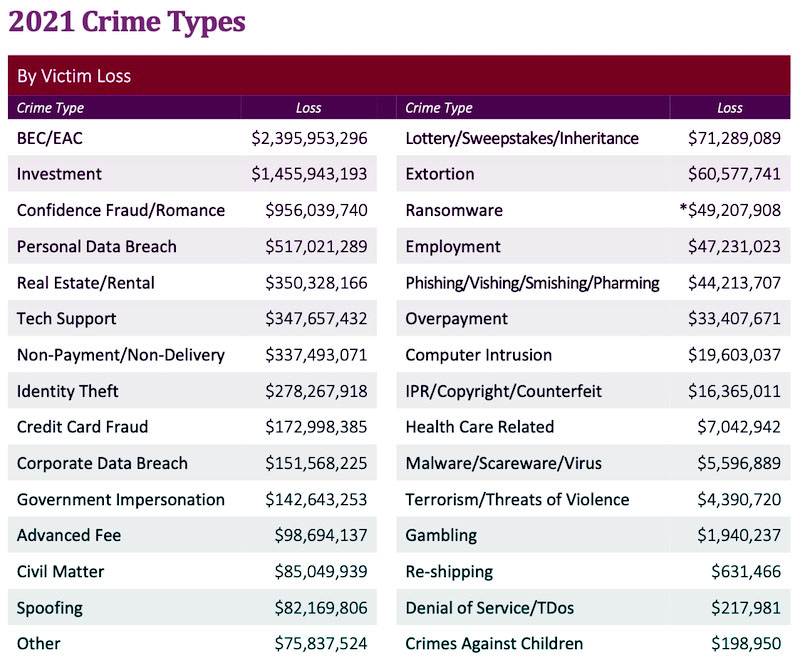
Source: FBI IC3
Learn how incident response planning boosts cyber resilience & security. GET THE EBOOK>>
BEC is a Chameleon
One of the things that makes BEC so challenging to defend against is that it’s slippery. BEC schemes can take many forms, making it especially tricky for employees to spot. Here are some common varities:
Invoice Scams
Fake invoice scams or urgent payment required scams are the most common BEC variations that employees will encounter. In this scenario, someone with the authority to pay vendors in an organization is sent a legitimate-looking invoice from a company that their organization does business with demanding immediate payment to avoid loss of goods or services. Barclays says that invoice scams accounted for 55% of the losses that they saw from SMB clients in Q1 2022, up 6% from 2021.
Gift cards and wire transfers
Money is the goal behind BEC. Cybercriminals will typically demand that payment for fraudulent reasons be transferred to them via wire transfer, cash app or gift card. An estimated 62% of BEC scams involve the cybercriminal asking for gift cards, cash app transfers or money cards. In a recent example, the FBI just busted a member of a criminal BEC gang in Florida for facilitating wire transfers of money that was defrauded from law firms and real estate companies to banks in South America.
Credential compromise scams
In this BEC variant, fraudsters will ask for the victim to provide credentials for a business account or access to a company’s systems or data, often on the pretense that they’ve misplaced credentials or weren’t given the right ones to complete a task. This was the case in a recent incident in Portland, Oregon. City officials said that an unauthorized party obtained access to a city government email account and transferred themselves a cool $1.4 million before the compromise was discovered.
See how ransomware rocks businesses in The Ransomware Road to Ruin. DOWNLOAD IT NOW>>
BEC is Attracting Top Talent Right Now
Ransomware has been the subject of many breathless headlines about cyberattacks, including major infrastructure attacks and nation-state cyberattacks. But all that press has led to an increase in scrutiny from law enforcement. Wired magazine recently warned that the combination of heavy scrutiny and high levels of law enforcement action around recent high-profile ransomware attacks are likely to push top ransomware groups into exploring new horizons. That will result in many skilled cybercriminals looking for a new way to make money, and BEC is a very attractive proposition. These bad actors can easily leverage their existing resources and skillset to shift operations into BEC. Social engineering is a critical component of BEC, and the bad guys have extensive expertise in that area. Ransomware groups also have the skills to easily establish “initial access” because they can call on their previous relationships with initial access brokers and other dark web resources. Plus, the software that they use is designed to be malleable, making it easy for them to jump in and conduct a successful attack quickly.
BEC & Phishing Go Hand in Hand
BEC scams often start with phishing. It’s an easy and cheap way for bad actors to get the ball rolling for most of today’s nastiest cyberattacks. Phishing is popular because it works, and employees are facing a flood of phishing threats every day. The number of recorded phishing attacks hit an all-time high in Q1 2022, with more than one million attacks in a quarter recorded for the first time. Phishing lures that are part of a BEC attack are often sophisticated, making it hard for employees to handle. An estimated 97% of employees cannot detect a sophisticated malicious message.
See the tide of phishing rise & fall to spot future trends in the eBook Fresh Phish. GET IT>>
7 Business Email Compromise Phishing Red Flags
BEC is very hard to spot but these red flags may indicate an attack.
Bad spelling, grammar and punctuation
Messages that use bad grammar, punctuation, spelling and usage are highly likely to be phishing messages that could be BEC attempts.
Unusual formatting, appearance or domain
BEC perpetrators often use spoofed or imitated email messages from a trusted sender as a lure. Be cautious about interacting with messages that look different than messages from that sender typically do. Also, make sure that an unexpected message comes from the sender’s real domain.
Improper greeting or signature
If the greeting, signature or contact information provided by the purported sender are unusual, that’s a strong indicator that the message is phishing and a potential BEC attack.
The sender will only communicate via email
Alarm bells should ring if attempts to communicate with the sender or verify their identity by phone or video conference are rebuffed.
The sender requests funds sent to an unusual address or in an unusual way
If an unanticipated message requests immediate payment or a transfer of funds to a different address, like a private email account, or in a different way, like cash app instead of check, that’s a hallmark of BEC.
The requested transactions are rushed or otherwise painted as urgent
Social engineering is a big part of BEC and cybercriminals will often try to create a sense of urgency about responding to their fraudulent message to manipulate victims into acting unwisely.
The sender is not using an official email address
If the message does not come from a company’s official email address or domain, like “[email protected]” instead of “[email protected]” it’s a good possibility that it’s actually a business email compromise attack.
How safe is your email domain? Find out now with our domain checker. CHECK YOUR DOMAIN>>
Gain Protection from BEC Attacks Automatically
In this dangerous world, every organization needs powerful email security that can stand up to the test of combatting today’s sophisticated threats without a high price tag. Graphus answers that call.
- Put 3 layers of protection between employees and dangerous phishing messages
- Automated email solutions like Graphus catch 40% more malicious messages than conventional solutions or a SEG.
- Cloud-native security harnesses machine learning to inform AI using a patented algorithm.
- Rely on real analysis, not just a problematic safe sender list.
- More than 50 points of comparison enable Graphus to sniff out targeted spear phishing, ransomware, zero-day attacks and other complex threats.
Stop phishing immediately with Graphus – the most simple, automated and affordable phishing defense available today. Contact one of our solutions specialists today










