These 5 Surging Ransomware Attacks Could Doom Your Organization
The business world has experienced several roadblocks in the last few years due to myriad factors including the COVID-19 pandemic, ongoing conflicts between countries and economic uncertainty. However, one thing that has shown no signs of stopping in these uncertain times is the onslaught of ransomware attacks that businesses are facing. If anything, these attacks are only on an upward trajectory.

Learn how incident response planning boosts cyber resilience & security. GET THE EBOOK>>
A successful ransomware attack has never been more expensive for a business
In 2022, ransomware attacks were at the root of 11% of breaches, up from 7.8% in 2021. Just one successful ransomware attack that leads to a data breach is an existential threat to any organization. The average cost of a ransomware-related data breach stands at $4.54 million, which can bring the curtains down for many companies. In fact, about 60% of SMBs go out of business within six months of a data breach or cyberattack, according to the United States Securities and Exchange Commission (SEC).
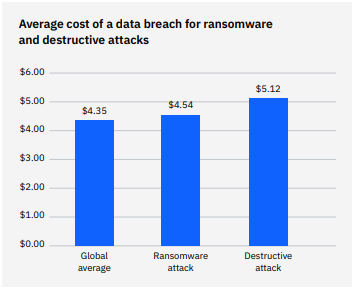
Source: FBI IC3
Explore today’s biggest threats & what’s next in The State of Email Security 2022 GET IT>>
Bad actors are evolving their tactics to bypass traditional security
Technology and new economic patterns read to evolution in every industry including cybercrime. Threat actors have continually evolved their ransomware playbook by varying their means and methods, embracing more reconnaissance and defense evasion techniques to evade an organization’s cybersecurity tools and measures. Here are some ransomware trends that have kept cybersecurity teams on edge this year.
Supply chain attacks: A supply chain attack is usually a third-party attack in which bad actors hunt for ways to steal a big company’s data or penetrate a big company’s defensive parameter without a direct attack. Instead, the bad guys will attack a service provider or supplier that may have less stringent security to gain data or access to the big company. Sometimes, bad actors will use that access to plant malware in a seemingly routine software update from a service provider. The infamous SolarWinds attack is a prime example. In that incident, a group believed to be Russia’s Cozy Bear gained access to U.S. government agencies’ secure systems through a compromised update to SolarWinds’ Orion software. The hacker group successfully gained access to computer systems belonging to multiple U.S. federal government departments including the U.S. Department of the Treasury.

Is your email security solution really getting the job done? This checklist helps you find out! GET CHECKLIST>>
Double extortion: This is today’s most common ransomware tactic. In a typical double extortion ransomware attack, cybercriminals encrypt information found on a system and then demand a ransom in exchange for a decryption key. However, with double extortion, attackers make multiple demands on the victim that cost money, increasing their payout. In this type of attack, the attackers may exfiltrate the data to a separate location in addition to encrypting it. Usually, they’ll threaten to sell or release the data on the dark web. But paying the bad guys doesn’t ensure the safety of your data. Less than 60% of companies that pay the ransom recover even part of their data, and 39% of companies that pay never see any of their data again.
Ransomware-as-a-Service (RaaS): Just like Software-as-a-Service (SaaS), RaaS is based around pay-for-use software, in this case, malware. Cybercriminals no longer need to write their own ransomware code; they can buy a ransomware kit from the dark web, which provides the necessary ransomware code and operational infrastructure to launch and maintain a ransomware campaign. Many ransomware gangs also provide services that include 24/7 support, bundled offers, user reviews, forums and other features identical to those offered by legitimate SaaS providers. Cybercriminal units, such as the DarkSide, REvil, and others, franchise their ransomware-as-a-service (RaaS) capabilities to other bad actors.

Get the guide that helps you detect & defeat dangerous BEC attacks to keep your company out of trouble! DOWNLOAD IT>>
Attack on unpatched systems: Unpatched systems are cybercriminals’ favored entrance route to breach an organization’s networks. They leverage zero-day vulnerabilities or take advantage of older known vulnerabilities that organizations are slow to identify and patch. Last year, there was a reported 29% rise in the exploitation of Common Vulnerabilities and Exposures (CVEs) associated with ransomware, and it can happen to any company that neglects its maintenance. For example, in July 2021, a global IT firm and one of the world’s largest tech consultancies, Accenture, was subjected to a ransomware attack by LockBit 2.0. The cybercriminal gang leveraged the IT company’s software vulnerabilities to launch its attack. Although the company denies paying any ransom, the attack damaged its brand reputation and customer trust.
Phishing: Phishing is one of the most common and devious techniques to launch ransomware attacks. One method is for an attacker to masquerade as a reputable entity or person in email or other forms of communication. to fool the recipient into falling for their tricks. Cybercriminals rely on social engineering techniques like creating urgency in the mind of the victim to lure that victim into clicking on a malicious attachment. Once the victim clicks on the attachment, cybercriminals gain access to their system and data and thereafter encrypt them to ask for ransom. n estimated 80% of IT professionals have seen a substantial increase in phishing attacks recently including those carrying ransomware.

See the state of email security in 2022 and the threats that should be on your radar in 2023. GET EBOOK>>
Protect Your Organization from Ransomware with Graphus
Ransomware attacks can debilitate your organization’s IT infrastructure with disastrous financial and operational consequences. As attacks become more aggressive, frequent, costly, and sophisticated, organizations must develop robust security strategies to thwart cybercriminals’ ill intentions.
Graphus is the world’s first AI-driven email security solution that automatically protects organizations from email-based ransomware attacks. The patented AI technology of Graphus creates a wall between organizations and cyberattacks, mitigating phishing attacks before it reaches their systems. It automatically monitors communication patterns between people, devices, and networks to reveal untrustworthy emails, making it a simple, powerful, and cost-effective automated phishing defense solution for companies of all sizes.
- Graphus blocks sophisticated phishing messages before users see them.
- Puts 3 layers of protection between employees and dangerous email messages.
- Seamlessly deploys to Microsoft 365 and Google Workspace via API without big downloads or lengthy installs.
- Provides intuitive reporting to help you gain insights into the effectiveness of your security, level of risks, attack types, and more
If you wish to know more about the Graphus Platform, Book a demo here.
NEW INTEGRATION! If you’re already using BullPhish ID for security and compliance awareness training and phishing simulations, you’ll love our latest integration Advanced Phishing Simulations (Drop-A-Phish). This feature leverages the power of integration with Graphus to eliminate the need for domain whitelisting and ensure 100% campaign deliverability to end users when running phishing simulations. LEARN MORE>>










