14 Types of Phishing Attacks and How to Protect Your Organization

As digitization becomes a part of our everyday lives, phishing scams have morphed into everyday occurrences. Most days, news websites are replete with organizations falling victim to cyberattacks through various phishing scams. Once a business suffers a phishing attack, it’s often challenging to recover from the sudden jolt as it adversely impacts both its finances and reputation. However, with knowledge and awareness, you can foil a cybercrime attempt on your business and protect yourself from any financial or reputational damage. Let’s dive deep into some common phishing attacks and how they can affect your business.
14 Types of Phishing Attacks
There are seemingly infinite variations of phishing with cybercriminals constantly trying new things. These are the most common varieties of phishing seen today.
Email phishing
It is arguably the most pervasive form of phishing, where cybercriminals try to steal sensitive information of the recipient via an email that appears to be from a legitimate source. Conducted en masse, email phishing targets several people in one go in the hope of duping as many as possible. The scammers encourage targets to click a link or download an attachment that has embedded malware. Once the recipient follows the cybercriminal’s instructions — downloading a malicious attachment or entering their credentials on a web link — the cybercriminal will have direct access to their systems and data. An instance of email phishing is a fake email from a bank asking you to click a link and verify your account details.
An example of email phishing:
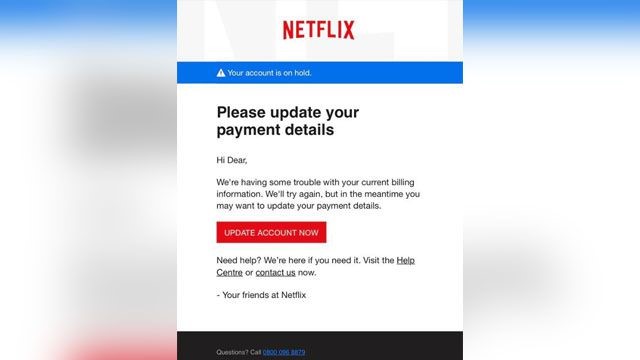
Source: FTC
Spear phishing
While most phishing attacks cast a wide net, spear phishing is a highly targeted, well-researched attack focused on business executives, public personalities and other high-ranking targets. Since spear phishing is a well-researched attack, cybercriminals use clever tactics, individually designed approaches and social engineering techniques to get victims’ attention and compel them to click on phishing links. For example, the FBI has released reports of spear phishing scams where the emails appeared to be from the National Center for Missing and Exploited Children.
A successful spear phishing attack can wreak havoc on organizations since high-ranking employees are usually victims of these attacks. Cybercriminals use this tactic to get hold of high-value data to reveal commercially sensitive information, manipulate stock prices or commit various acts of espionage.
Business email compromise (BEC)
A BEC attack begins with cybercriminals hacking or spoofing email accounts from a trusted business to fraudulently acquire money, personal information, financial details, payments, credit card numbers and other data from another firm. The scammers put extra effort into making the emails look authentic, and since it seems to come from a known authoritative figure, most of the employees comply with the demands of the attackers. The Federal Bureau of Investigation (FBI) declared BEC 64x worse than ransomware for businesses.
BEC attacks mainly rely on social engineering techniques, so antivirus, spam filters or email whitelisting are ineffective against it. However, with awareness, education and robust internal prevention techniques, especially for frontline staff, businesses can put a lid on BEC attacks.
Whaling
Whaling is when a cyberattack succeeds in trapping a “big fish,” like someone within the C-suite of a company. These attackers spend considerable time researching and profiling a high-value target for a sizeable reward. Recently, whaling emails have become highly sophisticated with the adoption of fluent business terminology, industry knowledge, personal references and spoofed email addresses. Even cautious eyes fail to identify a whaling email.
Vishing
Vishing is a cybercrime in which cybercriminals use phones to steal personal or financial information from victims. In this attack, they use savvy social engineering tactics to lure victims into giving up personal information and access to their bank accounts. Vishing attacks often include threatening calls and voicemails asking the recipient to call back immediately or run the risk of being arrested, having their bank accounts shut down or other scary outcomes.
Smishing
While vishing relies on phone calls, smishing uses a compelling SMS or text message to trick targeted recipients into clicking a link and sending the attacker private information or downloading malicious programs to a smartphone. Although Android and iOS security features stop most of the malware, no security controls can combat users who willingly send their confidential data to an unknown number.
HTTPS phishing
Although hypertext transfer protocol secure (HTTPS) links are often considered safe to click because they use encryption to increase security, cybercriminals are now leveraging them in their phishing emails to improve their authenticity. It is one of the most pernicious ways to launch a cyberattack and is currently the most prevalent method of delivering a malicious payload.
An example of HTTPS phishing is the well-known story of Sony Pictures. In 2014, the employees of Sony received fake Apple ID emails. Many employees disclosed their personal information, enabling hackers to infiltrate the company and steal passwords, logins and other valuable data.
Angler phishing
Social media has become part and parcel of our everyday lives. Even businesses leverage social media to communicate with their customers. Angler phishing is a new type of cyberattack where cybercriminals disguise themselves as customer service agents on social media to reach disgruntled customers of a company and obtain their personal information or account credentials under the pretense of alleviating their grievances.
Pharming
Pharming is a cyberattack in which attackers install malicious code on a personal computer or server that redirects users from the intended domain to fraudulent websites without their knowledge or consent. Using these websites, scammers compel users to divulge their credit card numbers, bank account numbers and other personal information for financial or credential theft.
Pop-up phishing
Pop-up phishing is a cyberattack in which fraudulent pop-ups trick users into installing malware on their systems. A typical pop-up phishing example is a warning pop-up on a user’s screen, informing users that their computer has been infected and the only way to remove the virus is by installing software.
Clone phishing
In a clone phishing attack, scammers create a nearly identical version of an email to trick their victims. They just change the attachment with their own that has malware or take the users to a fake website to extract personal information.
Evil twin phishing
An evil twin attack is a spoofing cyberattack that tricks users into connecting to a fake Wi-Fi access point, which mimics a legitimate network. Once a user is connected to an evil twin network, hackers have access to their network traffic, private login credentials and other secure information.
Trap phishing
Like most phishing attacks, trap phishing relies on human error to extract information or resources. Cybercriminals are constantly on the lookout for security flaws in an organization’s systems to trap or trick a user into downloading malware or giving away their personal or financial information.
Brand impersonation
Brand impersonation imitates a trusted brand to trick victims into responding and disclosing personal and sensitive information. Hackers use domain-spoofing techniques or lookalike domains to make their impersonation attempts convincing.
What is the most common form of phishing?
A famous saying goes, “There’s no school like the old school.” Unfortunately, the same goes for cybercrime as well. Along with the aforementioned advanced threats, old-fashioned phishing attacks, such as blast emails and spammy texts, still threaten businesses today. To this end, you need a cybersecurity solution that can protect your business against all kinds of threats.
Protect your organization from phishing attacks with Graphus
More than 90% of cyberattacks start with a phishing email to an unsuspecting victim. That’s why you need an advanced email security solution that can foil these attacks. Graphus is one such solution that leverages the power of AI to offer 360-degree security against all kinds of email-borne phishing attacks. It puts three layers of defense between a phishing email and your organization and prevents malicious emails from reaching an employee’s inbox.
Leveraging its patented AI technology, Graphus monitors communication patterns between people, devices and networks to reveal untrustworthy emails, making it a simple, powerful and cost-effective automated phishing defense solution for companies of all sizes. Graphus identifies and blocks various threats, including social engineering and zero-day attacks, to keep businesses safe from even the most sophisticated phishing threats.
- Graphus blocks sophisticated phishing messages before users see them.
- It puts three layers of protection between employees and dangerous email messages.
- It seamlessly deploys to Microsoft 365 and Google Workspace via API, without big downloads or lengthy installs.
- It provides intuitive reporting to help you gain insights into the effectiveness of your security, level of risks, attack types and more
Book a demo of Graphus to see how it protects your business from email-borne cyberattacks.
Explore today’s biggest threats & what’s next in The State of Email Security 2022 GET IT>>










