Why Should Businesses Create a Ransomware-Specific Incident Response Plan?

The stakes are high for firms dealing with today’s most competent hackers. Many of those competent hackers are in sophisticated cybercrime gangs that use ransomware to get the job done. One sucessful ransomware attack might result in a panoply of bad outcomes like costly downtime, the loss of critical data, brand harm and regulatory trouble and other expensive, exhausting nightmares. Having a ransomware-specific incident response plan is a major asset that can help reduce an attack’s effect by allowing businesses to respond quickly as well as reduce attack risk by shining a light on security flaws – and every organization should invest in one.
Explore today’s biggest threats & what’s next in The State of Email Security 2022 GET IT>>
Why Do We Need an Incident Response Plan at All?
Incident response planning is an underused security tool that brings an awesome array of benefits to the table, even if you never have to use your incident response plan. First and foremost, just having an incident response plan of any kind is a security win. How much of a difference can it make? An enormous difference. IBM researchers announced that just 39% of organizations with a formal, tested incident response plan experienced an incident, compared to 62% of those who didn’t have a plan. Plus, if the worst does happen, companies that have a formal, tested incident response plan can save 35% of the cost of an incident.
The faster a company can respond to an incident the better, and specialized attacks like a ransomware will require responders to take specific actions to mitigate the damage. Speedy response saves money and gives a company a head start on repairing the damage. Minimizing things like downtime and reputation damage is key to a successful recovery. Even if the immediate financial impact of downtime is minimal, if a ransomware assault disrupts services, the business’s brand is likely to suffer. Having a good ransomware response strategy in place means you are in a great position to accelerate your trip through the response cycle and start doing business normally again faster. Regular updating and review of incident response plans was a reason why cyber resiliency improved for 47% of high performers in the 2021 Cyber Resilient Organization Study by IBM.
See 10 reasons why Graphus is better than other email security solutions. SEE THE LIST>>
There’s No Time to Waste When it Comes to Ransomware
Discovering an attack quickly is of vital importance in incident response. After all, the more time the bad guys have to hang around, the more damage they can do. The average length of time that attackers spend with a victim company’s network before an attack is discovered is called the median dwell time, and that number is rapidly shrinking. Mandiant researchers have determined that the global median dwell time, or the number of days an attacker is in an environment before detection, has fallen to 24 days. Compare that to 2020’s global median dwell time of 56 days and it’s easy to see how the pace of attacks is escalating. Digging deeper, the median dwell time for incidents that did not involve ransomware was 45 days in 2021. But for ransomware investigations, it was only five days.
Unfortunately, many companies are failing to take advantage of the opportunity to get in front of a devastating cyber incident like a ransomware attack through advance planning. In the, IBM study, researchers determined that just over one-quarter of organizations have even made a cybersecurity incident response plan (CSIRP) of any kind that’s applied consistently across the entire enterprise. In the event of trouble, those companies will be left scrambling and out a lot of money that could have otherwise been saved. Worse yet, a paltry 50% of organizations that had incident response plans at all had a dedicated plan for an incident response to a ransomware attack. That’s asking for trouble in a world where 79% of respondents in a recent survey disclosed that their organization had experienced a ransomware attack in the last 12 months.
Learn the secret to ransomware defense in Cracking the RANSOMWARE Code. GET BOOK>>
Putting Together a Ransomware-Focused Incident Response Team
One critical part of developing an incident response plan is to assemble the right team. During a crisis, these are the people who receive the call. In a ransomware-specific plan, the people filling those roles will have relevant knowledge and skills to quickly act to stop the bleeding. One of the most widely-used incident response team structures is a Computer Security Incident Response Team (CSIRT). Creating your CSIRT, on the other hand, is not a one-size-fits-all answer. Each business has its own set of skills and resources. This basic structure can be tailored according to your organization’s needs.
The five primary functions of an incident response team are as follows:
Leadership – In times of crisis, leadership can make or break an organization. Leadership plays a huge role in executing an incident response plan. Leaders can ensure that everyone is on the same page and equipped with what they need to work well under pressure. Good leadership is vital for minimizing the impact of the attack on the company and its people, making sure that al of the bases are covered and pulling everyone as well as the company through the emergency successfully.
Investigation – You can’t start fixing a problem until you know what it is. Dispatching the right people to find a ransomware incursion and stop it quickly is vital. This arm of the team is responsible for leading the incident investigation to find the starting point of the attack, determining the extent of the damage and gathering relevant data to mitigate and remediate the incident. The data collected here also forms the foundation off an after action report.
Communications – It is critical to ensure that relevant internal and external messages reach the intended recipients. Someone needs to take point on handling any media attention and ensuring that accurate information flows to the right people. Fostering communication is essential between teams and departments inside the company as well as with external stakeholders. Keeping staffers reliably informed also reduces stress and powers down the rumor mill.
Documentation – This is a key role that cannot be overlooked. Everyone must be aware of the need to keep accurate records of all aspects of incident response. Those records are invaluable when a company sits down to assess the response effort and identify areas for improvement. Documentation may also be required for regulatory purposes.
Legal representation – An information security incident can have major legal ramifications. It is critical to ensure that incident response activities are carried out in line with existing laws and regulations. Legal guidance may also be needed to determine when and how to alert and update relevant authorities or if additional response or documentation steps must be taken for compliance purposes.
Add to your security team without adding to your headcount! LEARN MORE>>
Prepare (and Practice) a Response Plan
The most prominent set of industry best practices for cybersecurity incident response is maintained by the US National Institute of Standards and Technology (NIST). The agency’s four-part incident response cycle is the model that most organizations use to create their own incident response. The NIST incident response cycle divides the incident response cycle into four distinct steps that take you from start to finish when handling any cybersecurity incident. Using their framework will help ensure that an incident response plan including a ransomware-specific one will function smoothly.
The NIST Incident Response Cycle
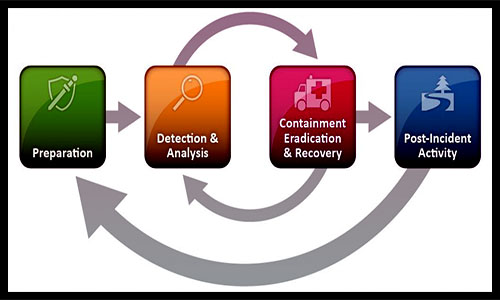
See how ransomware rocks businesses in The Ransomware Road to Ruin. DOWNLOAD IT NOW>>
Prevent Ransomware Attacks with Graphus
Graphus’ automated, AI-powered email security is an excellent choice for combating the stream of ransomware attacks destined for your firm. Automated email security like Graphus catches 40% more malicious messages than traditional security or an SEG (Secure Email Gateway), featuring three strong barriers between employees and malicious messages.
TrustGraph analyzes incoming communications using more than 50 different data points before allowing them to reach employee inboxes. TrustGraph also learns from each analysis it performs, adding that data to its knowledge base to continuously improve your security and learn without the need for human interaction.
EmployeeShield adds a bright, conspicuous box to potentially unsafe messages, informing employees of unexpected communications that may be unwanted and allowing employees to report that message with a single click for administrator scrutiny.
Phish911 enables employees to report any suspicious message that they receive instantly. When an employee reports an issue, the offending email is automatically quarantined for administrator review and deleted from everyone’s inbox, in addition to being removed from that employee’s inbox.










