4 Devious Phishing Scams to Watch Out For

Cybercrime is going through the roof, with big and small companies across a wide array of industries falling prey to phishing attacks every day. In the second quarter of 2022, the Anti Phishing Working Group (APWG) observed 1,097,811 total phishing attacks — the worst quarter for phishing that APWG has ever observed. However, it isn’t only the usual, run-of-the-mill phishing attacks that are putting the squeeze on business security. Hackers are constantly innovating new ways to put an organization’s systems and data in peril. These four recent clever phishing attacks show how cybercriminals are upping the ante of their cyberattack game.

Looking for a security rockstar? Get 5 superstar benefits for half the cost of the competition! SEE THE BENEFITS>>
BHL and USPS Shipping Scams
In these odd phishing scams, cybercriminals fraudulently impersonate the brand names of popular shipping companies to lure their victims into downloading malware onto their systems. In the BHL scam, the scammers borrowed the DHL company brand to trick the unwary — even going so far as to mimic its colors, logo, and web design. Many people reported receiving phishing emails that claimed a parcel-related alert message was waiting for them on a website, following which they were prompted to enter their personal information. The scammers were relying on people getting fooled just by replacing ‘D’ with a ‘B’.
A Sample BHL Scam Email:

Source: Reddit
While in the USPS scam, scammers posed as United States Postal Service (USPS) to send phishing emails informing recipients about discrepancies in their parcels. The email asked them to follow a link and enter their personal details to unblock their parcel delivery. Cybercriminals intended to use the information for monetary and identity theft.
A Sample USPS Scam Email:
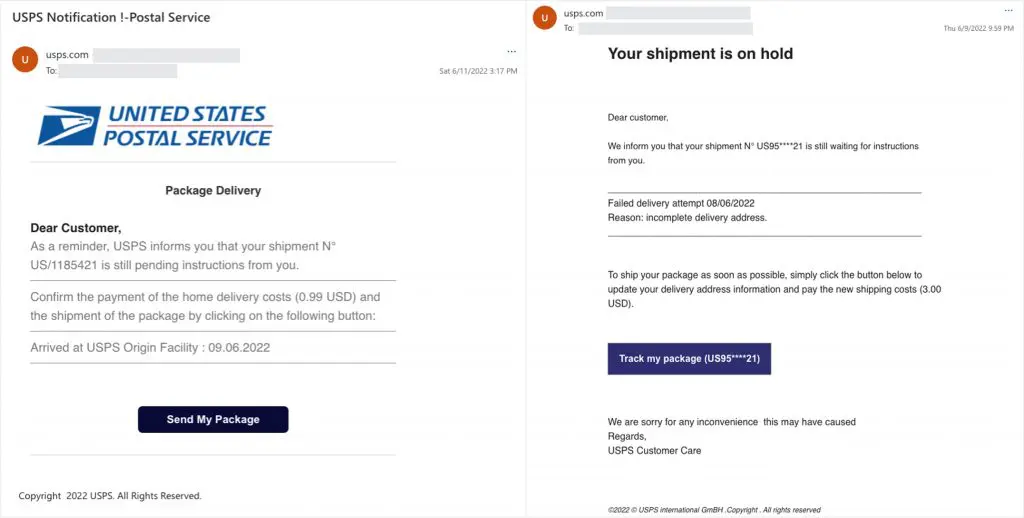
Source: Reddit

Learn how to add more hands to your security team without adding to your headcount. FREE EBOOK>>
Various Kinds of Cryptocurrency Theft
Cryptocurrency is the preferred monetary unit on the dark web. It’s the payment method of choice for cybercriminals as it is practically impossible to trace. With the growing adoption of cryptocurrency, cybercriminals are using many social engineering lures to trap their targets into handing some over. One such attack is an attempt to steal usernames and passwords using credential harvesting. In this method, the cybercriminals deliver a concealed URL in the email, which redirects to a credential harvesting landing page. Once the email recipient enters his details on the landing page, scammers have direct access to their cryptocurrency wallets.
In another type of cryptocurrency theft, the victim receives an email from a hacker claiming to have gained control of their computer and online accounts with malware. The scammers claim to have access to audio and video recordings of the user, alongside their browsing history. They try to blackmail the victims into paying bitcoins, failing which they threaten to release this information on the web. But in reality, the attacker might have sent out spam emails to as many users as possible, hoping to trick some victims into making the payment. Requests for cryptocurrency also becoming commonplace in business email compromise (BEC) scams, where scammers pose as a trusted colleague or business partner, asking the victim to transfer a large number of cryptocurrency coins to complete an essential and time-sensitive deal.

Get the guide that helps you detect & defeat dangerous BEC attacks to keep your company out of trouble! DOWNLOAD IT>>
Emails Claiming Copyright Infringement
This is a devious scam often used to spread LockBit ransomware works via emails claiming that the victim has engaged in copyright infringement. Often directed to the website operators, these emails inform them that they have used copyrighted content on their platform unlawfully. Subsequently, the administrator has to enquire about the claim and remove the files if the claim stands true. However, the link refers to a password-protected ZIP archive containing a compressed file, which prevents its detection by security tools. Upon clicking on the file, a LockBit 2.0 encryption Trojan is installed on their systems. Once the ransomware is installed, it keeps running on the system, even after a reboot or desktop change. Eventually, bad actors demand that the victim pay the ransom to get their systems up and running. Copyright infringement scams are also popular on social media sites, especially Instagram.

Learn the ins and outs of today’s wide variety of phishing attacks & how to stop them in Phishing 101. DOWNLOAD IT>>
Cleverly Hidden Malicious HTML Attachments to Install Malware
Most businesses send and receive emails with HTML attachments. Unremarkable messages like system-generated email reports regularly have HTML attachments embedded in them. Hackers have found a way to leverage this information to launch phishing attacks on businesses. Several businesses have reported receiving phishing emails disguised as standard messages with seemingly harmless HTML attachments that slip past their security to deliver malware. These phishing emails are tough to detect as the HTML attachments themselves are not malicious, so they sail through many security checkpoints. The attachments contain a link, which, when opened, requests the users to enter their credentials to access information. But in reality, they are now downloading a file that contains malware. HTML attachments have been one of the more successful techniques because hackers no longer need to include malicious links in an email, allowing them to bypass most anti-spam and anti-virus precautions easily.
Learn the secret to building a strong ransomware defense in Cracking the RANSOMWARE Code. GET BOOK>>
AI-Driven Email Security is the Future
Although a SG or onboard security in Microsoft 365 or Google Workspace might save you from some cyberattacks, they’re no match for some of today’s trickiest and most innovative phishing attacks. Cybercriminals are getting creative and using advanced tools to launch some of the most sophisticated cyberattacks on businesses, irrespective of their size. Even big conglomerates have fallen into the traps of cybercriminals recently. That’s why you need to be a step ahead of them to secure your business against all kinds of adversities.
Graphus’s AI-driven, automated email security can help you stay miles ahead of cybercriminals. It puts three layers of defense between a phishing email and your organization and prevents any phishing email from reaching an employee’s inbox. Graphus stands tall against all kinds of social engineering lures, leveraging its patented AI technology to catch threats others miss including zero-day attacks. It monitors communication patterns between people, devices and networks to reveal untrustworthy emails, making it a simple, powerful, and cost-effective automated phishing defense solution for companies of all sizes.
- Graphus blocks 99.9% of sophisticated phishing messages before they reach an employee’s inbox. Puts 3 layers of protection between employees and dangerous email messages.
- Seamlessly deploys to Microsoft 365 and Google Workspace via API, without big downloads or lengthy installs.
- Provides intuitive reporting to help you gain insights into the effectiveness of your security, level of risks, attack types, and more
- Book a demo of Graphus










